OpenDaylight Virtual Tenant Network (VTN) adalah aplikasi yang menyediakan multi-tenant virtual network pada SDN controller.

Biasanya Jaringan berbasis tenant sering diimplementasikan di tempat-tempat publik seperti bandara, perkantoran dimana disana terdapat banyak pelangan yang harus diisolasi networknya, sebagai contoh misalnya pada sebuah bandara terdapat beberapa maskapai, antar maskapai jaringannya harus diisolasi walaupun secara fisik jaringanya terpusat pada satu switch namun secara logic sebenernya jaringanya terpisah.
nah, kalo VTN (virtual tenant network) sebenarnya sama seperti jaringan berbasis tenant pada umumnya, bedanya Opendaylight VTN adalah semua konfigurasi VTN dilakukan di Controller SDN sehingga menjadi terpusat dan mengunakan protocol RESTCONF untuk push confignya.
selain itu keunikan VTN adalah logical abstraksi plane dengan ini mengmungkinkan memisahka logic plane dengan physical plane. Pengguna dapat merancang dan menerapkan jaringan yang diinginkan tanpa mengetahui topologi jaringan fisik atau pembatasan bandwidth.
Komponen utama pada VTN adalah
- VTN Manager
- VTN Coordinator
VTN Manager adalah pluguin di opendaylight yang dapat berinteraksi dengan modul lain untuk mengaktifkan fitur VTN di opendaylight SDN controller. ini juga menyediakan interface REST API untuk mengkonfigurasi komponen VTN di opendaylight, protocol ini sering disebut RestConf. Selain iu VTN juga dapat di implementasikan di openstack untuk memisahkan jaringan antar tenant.
Fitur pada VTN manager :
- Odl-vtn-manager => menyediakan API JAVA dari VTN Manager.
- Odl-vtn-manager-rest => menyediakan API REST dari VTN Manager.
- Odl-vtn-manager-neutron => menyediakan integrasi dengan antarmuka Neutron.
VTN Coordinator adalah aplikasi eksternal yang menyediakan antarmuka REST bagi pengguna untuk menggunakan OpenDaylight VTN Virtualization. VTN Coordinator berinteraksi dengan VTN Manager. biasanya VTN Coordinator dapat mengkoordinasikan beberapa vtn manager.
Contoh penerapan VTN manager

Bisa dilihat dari paparan diatas secara physical plane dari h1 ke h3 harus melewati 3 switch namun dari pandangan VTN dari h1 ke h3 hanya melewati virtual bridge, itulah yang disebut bahwa penguna tidak perlu tahu jaringan fisiknya. Ayooo langsung kita mulai saja ngelabnya 😀
LAB GNS3
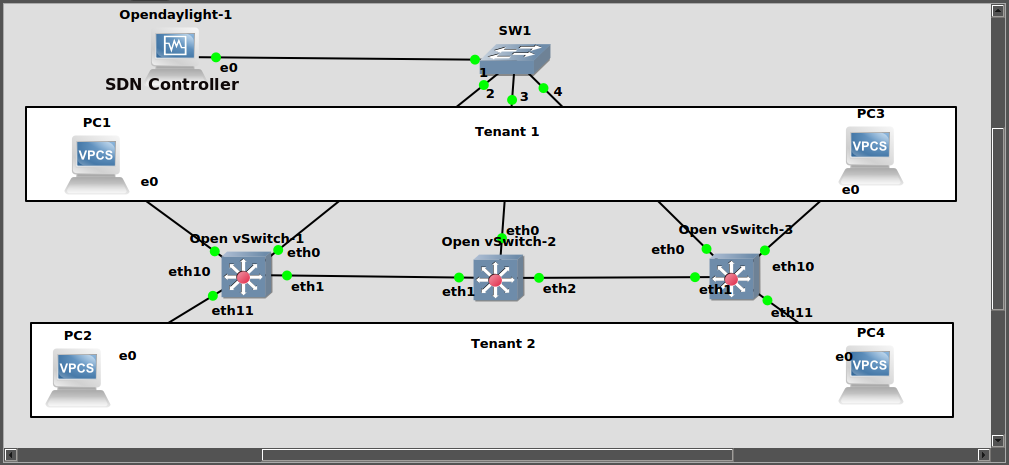
Pada lab Ini kita butuh :
1 SDN Controller (Opendaylight Boron SR3), 3 OpenvSwitch, 4 VPCS (sebagai client)
untuk menginstall openvswitch di GNS3 bisa liat disini
Setting IP Address pada VPCS
|
1 2 3 4 |
PC1 => 10.212.113.10/24 PC2 => 10.212.113.20/24 PC3 => 10.212.113.30/24 PC4 => 10.212.113.40/24 |
Installasi Opendaylight di Centos
IP Management SDN Controller = 10.10.10.1/24 (Generic Driver – Udp tunnel dari GNS3)
IP external = 192.168.21.100/24 (Host Only Adapter)
|
1 2 3 4 5 |
yum -y install java-1.8.0-openjdk wget -c https://nexus.opendaylight.org/content/repositories/opendaylight.release/org/opendaylight/integration/distribution-karaf/0.5.2-Boron-SR2/distribution-karaf-0.5.2-Boron-SR2.tar.gz tar -xf distribution-karaf-0.5.3-Boron-SR3.tar.gz -C /opt /opt/distribution-karaf-0.5.3-Boron-SR3/bin/karaf feature:install odl-dlux-all odl-vtn-manager odl-vtn-manager-rest |
Buka Web Browser
|
1 2 3 4 |
Login ke WebUI DLUX http://192.168.21.100:8181/index.html username : admin password : admin |
Openvswitch-1
Konfigurasi pertama pada openvswitch adalah memberikan ip management untuk berkomunikasi dengan SDN Controller
Mapping Interface
|
1 2 3 4 |
eth0 => controller eth1 => openvswitch-2 eth10 => PC1 eth11 => PC2 |
Ubah port eth1 ke br1 (secara default semua port di ovs ada di br0)
|
1 2 |
ovs-vsctl del-port br0 eth0 ovs-vsctl add-port br1 eth0 |
ini dipisahkan karena berfungsi sebagai interface management sehingga tidak digabuung dalam interface access. setelah itu set ip di eth0
|
1 2 3 4 5 6 7 |
vi /etc/network/interfaces ........... auto eth0 iface eth0 inet static address 10.10.10.10 netmask 255.255.255.0 ........... |
setelah itu aktifkan interface eth0 dan test ping ke ip sdn controller
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
/ # ifup eth0 / # ping 10.10.10.1 PING 10.10.10.1 (10.10.10.1): 56 data bytes 64 bytes from 10.10.10.1: seq=0 ttl=64 time=0.782 ms 64 bytes from 10.10.10.1: seq=1 ttl=64 time=0.609 ms 64 bytes from 10.10.10.1: seq=2 ttl=64 time=0.541 ms 64 bytes from 10.10.10.1: seq=3 ttl=64 time=0.533 ms 64 bytes from 10.10.10.1: seq=4 ttl=64 time=0.600 ms 64 bytes from 10.10.10.1: seq=5 ttl=64 time=0.629 ms ^C --- 10.10.10.1 ping statistics --- 6 packets transmitted, 6 packets received, 0% packet loss round-trip min/avg/max = 0.533/0.615/0.782 ms |
Set br0 ke SDN controller
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
/ # ovs-vsctl set-controller br0 tcp:10.10.10.1:6633 / # ovs-vsctl show 897a3970-298f-4a07-bd0d-949489ace3fb Bridge "br0" Controller "tcp:10.10.10.1:6633" is_connected: true Port "eth5" Interface "eth5" Port "eth9" Interface "eth9" Port "eth7" Interface "eth7" Port "eth4" Interface "eth4" Port "eth11" Interface "eth11" Port "eth1" Interface "eth1" Port "br0" Interface "br0" type: internal Port "eth8" Interface "eth8" Port "eth10" Interface "eth10" Port "eth14" Interface "eth14" Port "eth15" Interface "eth15" Port "eth6" Interface "eth6" Port "eth12" Interface "eth12" Port "eth13" Interface "eth13" Bridge "br1" Port "br1" Interface "br1" type: internal Port "eth0" Interface "eth0" Bridge "br3" Port "br3" Interface "br3" type: internal Bridge "br2" Port "br2" Interface "br2" type: internal |
Dump-Flow Br0
|
1 2 3 |
/ # ovs-ofctl dump-flows -O openflow13 br0 OFPST_FLOW reply (OF1.3) (xid=0x2): cookie=0x7f57ffffffffffff, duration=7397.056s, table=0, n_packets=1513, n_bytes=171456, send_flow_rem priority=0 actions=CONTROLLER:65535 |
karena dari controller belum ada push flow, maka pada br0 hanya ada flow ke controller saja
untuk openvswitch-2 dan openvswitch-3 lakukan seperti openvswitch1 hanya bedakan ipnya saja
Openvswitch-2
Mapping Interface
|
1 2 3 4 |
eth0 => controller eth1 => openvswitch-1 eth2 => openvswitch-3 IP Management => 10.10.10.11/24 |
Set br0 ke SDN controller
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
/ # ovs-vsctl set-controller br0 tcp:10.10.10.1:6633 / # ovs-vsctl show 88d6a2dd-2aa0-410d-99e4-f563e380988f Bridge "br3" Port "br3" Interface "br3" type: internal Bridge "br1" Port "eth0" Interface "eth0" Port "br1" Interface "br1" type: internal Bridge "br2" Port "br2" Interface "br2" type: internal Bridge "br0" Controller "tcp:10.10.10.1:6633" is_connected: true Port "eth4" Interface "eth4" Port "eth6" Interface "eth6" Port "eth12" Interface "eth12" Port "eth13" Interface "eth13" Port "eth1" Interface "eth1" Port "eth8" Interface "eth8" Port "eth14" Interface "eth14" Port "eth7" Interface "eth7" Port "eth10" Interface "eth10" Port "eth2" Interface "eth2" Port "eth11" Interface "eth11" Port "eth5" Interface "eth5" Port "eth15" Interface "eth15" Port "eth9" Interface "eth9" Port "eth3" Interface "eth3" Port "br0" Interface "br0" type: internal |
Dump-Flow Br0
|
1 2 3 |
/ # ovs-ofctl dump-flows -O openflow13 br0 OFPST_FLOW reply (OF1.3) (xid=0x2): cookie=0x7f57ffffffffffff, duration=7599.399s, table=0, n_packets=3075, n_bytes=346201, send_flow_rem priority=0 actions=CONTROLLER:6553 |
Openvswitch-3
Mapping Interface
|
1 2 3 4 5 |
eth0 => controller eth1 => openvswitch-2 eth10 => PC3 eth11 => PC4 IP Management => 10.10.10.12/24 |
Set br0 ke SDN controller
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
/ # ovs-vsctl set-controller br0 tcp:10.10.10.1:6633 / # ovs-vsctl show 88d6a2dd-2aa0-410d-99e4-f563e380988f Bridge "br3" Port "br3" Interface "br3" type: internal Bridge "br1" Port "eth0" Interface "eth0" Port "br1" Interface "br1" type: internal Bridge "br2" Port "br2" Interface "br2" type: internal Bridge "br0" Controller "tcp:10.10.10.1:6633" is_connected: true Port "eth4" Interface "eth4" Port "eth6" Interface "eth6" Port "eth12" Interface "eth12" Port "eth13" Interface "eth13" Port "eth1" Interface "eth1" Port "eth8" Interface "eth8" Port "eth14" Interface "eth14" Port "eth7" Interface "eth7" Port "eth10" Interface "eth10" Port "eth2" Interface "eth2" Port "eth11" Interface "eth11" Port "eth5" Interface "eth5" Port "eth15" Interface "eth15" Port "eth9" Interface "eth9" Port "eth3" Interface "eth3" Port "br0" Interface "br0" type: internal |
Dump-Flow Br0
|
1 2 3 |
/ # ovs-ofctl dump-flows -O openflow13 br0 OFPST_FLOW reply (OF1.3) (xid=0x2): cookie=0x7f57ffffffffffff, duration=7599.399s, table=0, n_packets=3075, n_bytes=346201, send_flow_rem priority=0 actions=CONTROLLER:6553 |
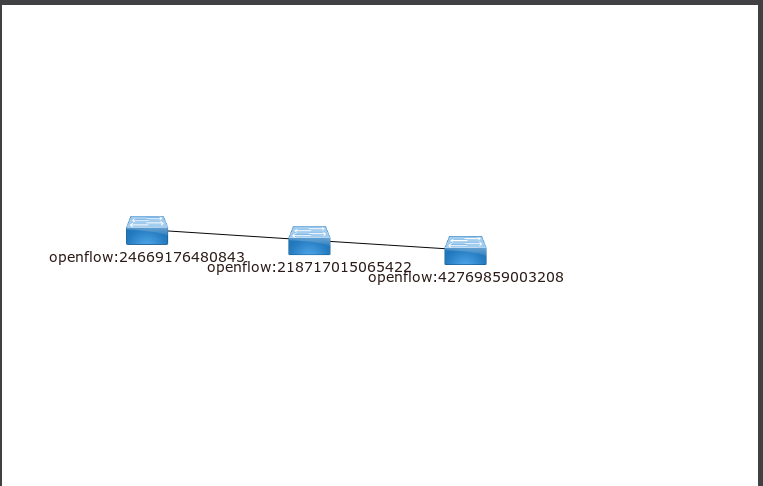
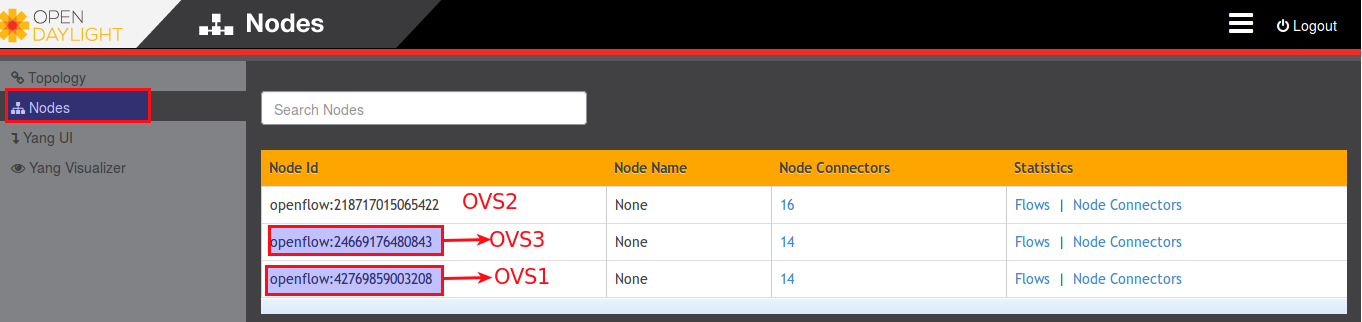
Melihat dari Dashboard Opendaylight
terdapat 3 switch openflow yang sudah terhubung ke sdn controller.
Test Ping PC1 ke semua PC (sebelum di set VTN)
|
1 2 3 4 5 6 |
PC1> ping 10.212.113.20 host (10.212.113.20) not reachable PC1> ping 10.212.113.30 host (10.212.113.30) not reachable PC1> ping 10.212.113.40 host (10.212.113.40) not reachable |
secara default semua koneksi tidak terhubung karena belum ada flow pada masing2 switch openflow (use ovs)
Konfigurasi VTN di Controller mengunakan REST API (Restconf), saya akan menghubungkan PC1 ke PC3
PC1 ================= vBridge ============== PC3
Membuat Tenant Baru, dengan nama vtn1
|
1 2 |
[root@opendaylight ~]# curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:8181/restconf/operations/vtn:update-vtn -d '{"input":{"tenant-name":"vtn1"}}' {"output":{"status":"CREATED"}} |
Membuat Bridge dengan nama vbr1 pada vtn1
|
1 2 |
[root@opendaylight ~]# curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:8181/restconf/operations/vtn-vbridge:update-vbridge -d '{"input":{"tenant-name":"vtn1", "bridge-name":"vbr1"}}' {"output":{"status":"CREATED"}} |
Membuat dua interface pada bridge vbr1 utnuk menghubungkan PC1 ke PC3
|
1 2 3 4 |
[root@opendaylight ~]# curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:8181/restconf/operations/vtn-vinterface:update-vinterface -d '{"input":{"tenant-name":"vtn1", "bridge-name":"vbr1", "interface-name":"if1"}}' {"output":{"status":"CREATED"}} [root@opendaylight ~]# curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:81erface:update-vinterface -d '{"input":{"tenant-name":"vtn1", "bridge-name":"vbr1", "interface-name":"if2"}}' {"output":{"status":"CREATED"}} |
Langkah terkahir, lakukan Mapping interface if1 dan if2 ke openflow switch ( dalam hal ini openvswitch)
PC1 ======================(if1)vBridge(if2)====================== PC2
Untuk step akhir ini kita harus liat dari dashboard opendaylight
Mapping interface eth10 pada ovs1 ke interface if1
|
1 2 |
[root@opendaylight ~]# curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:8181/restconf/operations/vtn-port-map:set-port-map -d '{"input":{"tenant-name":"vtn1", "bridge-name":"vbr1", "interface-name":"if1", "node":"openflow:42769859003208", "port-name":"eth10"}}' {"output":{"status":"CREATED"}} |
Mapping interface eth10 pada ovs3 ke interface if2
|
1 2 |
[root@opendaylight ~]#curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:8181/restconf/operations/vtn-port-map:set-port-map -d '{"input":{"tenant-name":"vtn1", "bridge-name":"vbr1", "interface-name":"if2", "node":"openflow:24669176480843", "port-name":"eth10"}}' {"output":{"status":"CREATED"}} |
Tahap terkahir adalah testing Ping PC1 (10.212.113.10) ke PC3 (10.212.113.30)
|
1 2 3 4 5 6 7 8 9 10 11 12 |
PC1> ping 10.212.113.30 84 bytes from 10.212.113.30 icmp_seq=1 ttl=64 time=25.575 ms 84 bytes from 10.212.113.30 icmp_seq=2 ttl=64 time=1.454 ms 84 bytes from 10.212.113.30 icmp_seq=3 ttl=64 time=1.894 ms 84 bytes from 10.212.113.30 icmp_seq=4 ttl=64 time=1.340 ms 84 bytes from 10.212.113.30 icmp_seq=5 ttl=64 time=1.519 ms PC1> ping 10.212.113.20 host (10.212.113.20) not reachable PC1> ping 10.212.113.40 host (10.212.113.40) not reachable |
Berhasil!, PC1 dapat ping PC3 namun tidak bisa ping ke host yang lain karena tidak ada flow yang mengarah ke PC yg lain, mari kita lihat flow dimasing-masing OVS
Flow OpenvSwitch1
|
1 2 3 4 5 |
/ # ovs-ofctl dump-flows -O openflow13 br0 OFPST_FLOW reply (OF1.3) (xid=0x2): cookie=0x7f56000000000005, duration=123.404s, table=0, n_packets=5, n_bytes=490, send_flow_rem priority=10,in_port=2,vlan_tci=0x0000/0x1fff,dl_src=00:50:79:66:68:02,dl_dst=00:50:79:66:68:00 actions=output:11 cookie=0x7f56000000000006, duration=123.372s, table=0, n_packets=4, n_bytes=392, idle_timeout=300, send_flow_rem priority=10,in_port=11,vlan_tci=0x0000/0x1fff,dl_src=00:50:79:66:68:00,dl_dst=00:50:79:66:68:02 actions=output:2 cookie=0x7f57ffffffffffff, duration=12363.036s, table=0, n_packets=2558, n_bytes=288352, send_flow_rem priority=0 actions=CONTROLLER:65535 |
Flow OpenvSwitch2
|
1 2 3 4 5 |
/ # ovs-ofctl dump-flows -O openflow13 br0 OFPST_FLOW reply (OF1.3) (xid=0x2): cookie=0x7f56000000000005, duration=152.372s, table=0, n_packets=5, n_bytes=490, send_flow_rem priority=10,in_port=3,vlan_tci=0x0000/0x1fff,dl_src=00:50:79:66:68:02,dl_dst=00:50:79:66:68:00 actions=output:2 cookie=0x7f56000000000006, duration=152.352s, table=0, n_packets=4, n_bytes=392, send_flow_rem priority=10,in_port=2,vlan_tci=0x0000/0x1fff,dl_src=00:50:79:66:68:00,dl_dst=00:50:79:66:68:02 actions=output:3 cookie=0x7f57ffffffffffff, duration=12467.247s, table=0, n_packets=5133, n_bytes=573615, send_flow_rem priority=0 actions=CONTROLLER:65535 |
Flow OpenvSwitch3
|
1 2 3 4 5 |
/ # ovs-ofctl dump-flows -O openflow13 br0 OFPST_FLOW reply (OF1.3) (xid=0x2): cookie=0x7f56000000000005, duration=182.447s, table=0, n_packets=5, n_bytes=490, idle_timeout=300, send_flow_rem priority=10,in_port=11,vlan_tci=0x0000/0x1fff,dl_src=00:50:79:66:68:02,dl_dst=00:50:79:66:68:00 actions=output:2 cookie=0x7f56000000000006, duration=182.439s, table=0, n_packets=4, n_bytes=392, send_flow_rem priority=10,in_port=2,vlan_tci=0x0000/0x1fff,dl_src=00:50:79:66:68:00,dl_dst=00:50:79:66:68:02 actions=output:11 cookie=0x7f57ffffffffffff, duration=12470.863s, table=0, n_packets=2646, n_bytes=301410, send_flow_rem priority=0 actions=CONTROLLER:6553 |
Bisa diliat pada masing-masing ovs sudah terdpat flow yang dipush melalui controller SDN (itu yang namanya asbtraction dimana kita tidak perlu config langsung ke device namun cukup di controller saja)
Hasil REST di Controller SDN Opendaylight
#verfikasi configurasi by rest API
|
1 |
curl --user "admin":"admin" -H "Content-type: application/json" -X GET http://192.168.21.100:8181/restconf/operational/vtn:vtns/ |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 |
{ "vtns": { "vtn": [ { "name": "vtn1", "vtenant-config": { "idle-timeout": 300, "hard-timeout": 0 }, "vbridge": [ { "name": "vbr1", "vbridge-config": { "age-interval": 600 }, "bridge-status": { "state": "UP", "path-faults": 0 }, "vinterface": [ { "name": "if1", "vinterface-status": { "state": "UP", "mapped-port": "openflow:42769859003208:11", "entity-state": "UP" }, "port-map-config": { "node": "openflow:42769859003208", "port-name": "eth10", "vlan-id": 0 }, "vinterface-config": { "enabled": true } }, { "name": "if2", "vinterface-status": { "state": "UP", "mapped-port": "openflow:24669176480843:11", "entity-state": "UP" }, "port-map-config": { "node": "openflow:24669176480843", "port-name": "eth10", "vlan-id": 0 }, "vinterface-config": { "enabled": true } } ] } ] } ] } } |
kalau ingin menghapus caranya sperti ini
|
1 |
curl --user "admin":"admin" -H "Content-type: application/json" -X POST http://192.168.21.100:8181/restconf/operations/vtn:remove-vtn -d '{"input":{"tenant-name":"vtn1"}}' |
mungkin cukup sekian dulu untuk tutorialnya, initnya setiap controller SDN mempunya karaktersitik tersendiri seperti opendaylight, onos dan floodlight. jadi kita dapat mengunakan controller tersebut sesuai dengan kebutuhkan kita.
Ref : docs.opendaylight.org/en/stable-boron/user-guide/virtual-tenant-network-(vtn).html
Sekian wassalamualaikum
Komentar