Jadi apa yang penting untuk anda ketahui mengenai FirewallD? Apa yang bisa anda lakukan dengan firewallD? That’s just a quick question? Right, at this post will cover of all it 🙂 mari kita lanjtkan haha
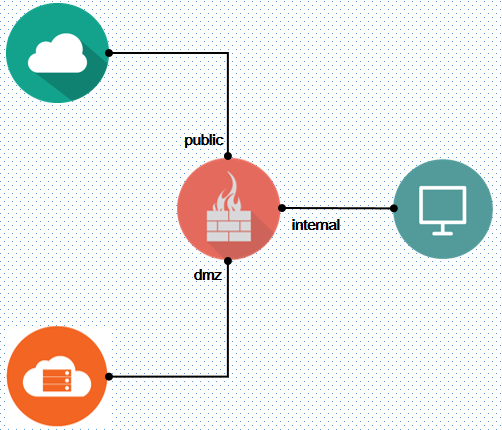
gambar diatas akan mewakili apa yang kita lakukan dengan firewallD (klo kurang jelas yuk ikuti tulisannya hehe)
Essential 1: Basic Operation
a. Enable firewallD:
|
1 2 |
[root@Centos-FW ~]# systemctl enable firewalld [root@Centos-FW ~]# systemctl start firewalld |
b. Cek status:
|
1 |
systemctl status firewalld |
Output:
|
1 2 3 4 5 6 |
firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled) Active: active (running) since Sun 2017-01-08 05:48:21 EST; 12h ago Main PID: 6583 (firewalld) CGroup: /system.slice/firewalld.service └─6583 /usr/bin/python -Es /usr/sbin/firewalld --nofork --nopid |
c. Reload konfigurasi: saat anda melakukan perubahan pastikan anda melakukan reload supaya perubahan itu jalan.
|
1 2 |
[root@Centos-FW ~]# firewall-cmd --reload success |
Pastikan outputnya success, yang menandakan perubahan atau reload itu berhasil.
d. Cek Zone
quick view:
|
1 2 |
[root@Centos-FW ~]# firewall-cmd --get-zones block dmz drop external home internal public trusted work |
by default di firewalld sudah ada predefined zone, tapi anda juga bisa menambahkan zone sendiri sesuai yang anda inginkan.
detail:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
[root@Centos-FW ~]# firewall-cmd --list-all-zone block interfaces: sources: services: ports: masquerade: no forward-ports: icmp-blocks: rich rules: dmz (active) interfaces: eno33554984 sources: services: ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: <em>[Output cut]</em> |
cek spesifik zone with all detail info:
|
1 2 3 4 5 6 7 8 9 10 |
[root@Centos-FW ~]# firewall-cmd --zone=dmz --list-all dmz (active) interfaces: eno33554984 sources: services: ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: |
cek spesifik zone with specific info:
|
1 2 3 4 5 6 7 8 9 |
[root@Centos-FW ~]# firewall-cmd --zone=public --list-interface eno16777736 [root@Centos-FW ~]# firewall-cmd --zone=public --list-port 4500/tcp 500/udp 4500/udp [root@Centos-FW ~]# firewall-cmd --zone=public --list-services dhcpv6-client dns ftp http https ssh telnet [root@Centos-FW ~]# firewall-cmd --zone=public --list-rich-rules rule family="ipv4" source address="172.16.0.0/24" destination address="0.0.0.0/0" port port="443" protocol="tcp" reject rule family="ipv4" source address="172.16.0.0/24" destination address="0.0.0.0/0" port port="80" protocol="tcp" accept |
2. Essential 2 : Change Operation (Add, Remove/Change)
Jika tadi diatas anda sudah dapat melakukan show rule, setting default firewalld, maka pada bagian kedua ini perubahan apa yang bisa anda lakukan sebagai contoh menambah zone, interface, port, rule dan lain-lain, begitu juga halnya anda ingin menghapus atau remove interface pada sebuah zone, atau menghapus zone itu sendiri. mari kita lihat satu persatu:
a. Menambah zone:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
[root@Centos-FW ~]# firewall-cmd --permanent --new-zone=IT success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=IT --list-all IT interfaces: sources: services: ports: masquerade: no forward-ports: icmp-blocks: rich rules: |
b. Menambah Interface Pada Zone IT
Untuk menambah interface anda cukup tambahkan command –add-interfce=nama_interface, jika anda lupa nama interfacenya, anda bisa show interface dengan command ip add show
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
[root@Centos-FW ~]# firewall-cmd --zone=IT --add-interface=lo --permanent success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=IT --list-all IT (active) interfaces: lo sources: services: ports: masquerade: no forward-ports: icmp-blocks: rich rules: |
Cara yang lain untuk menambah zone, anda bisa add di config interface seperti berikut:
|
1 2 |
[root@Centos-FW ~]# more /etc/sysconfig/network-scripts/ifcfg-eno16777736 | grep ZONE ZONE=public |
c. Menambah Port, Service, Source
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
[root@Centos-FW ~]# firewall-cmd --zone=IT --permanent --add-port=2017/tcp success [root@Centos-FW ~]# firewall-cmd --zone=IT --permanent --add-service=ftp success [root@Centos-FW ~]# firewall-cmd --zone=IT --permanent --add-service=http success [root@Centos-FW ~]# firewall-cmd --zone=IT --permanent --add-source=192.168.254.1 success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=IT --list-all IT (active) interfaces: lo sources: 192.168.254.1 services: ftp http ports: 2017/tcp masquerade: no forward-ports: icmp-blocks: rich rules: |
d. Melakukan remove dan Change interface
Ini misal anda ingin ubah interface, menghapus interface pada zone, dan lain-lain. saya beri contoh satu ja ya 🙂
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 |
[root@Centos-FW ~]# firewall-cmd --zone=IT --change-interface=lo.0 --permanent success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=IT --list-all IT (active) interfaces: lo lo.0 sources: 192.168.254.1 services: ftp http ports: 2017/tcp masquerade: no forward-ports: icmp-blocks: rich rules: [root@Centos-FW ~]# firewall-cmd --zone=IT --remove-interface=lo --permanent success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=IT --list-all IT (active) interfaces: lo lo.0 sources: 192.168.254.1 services: ftp http ports: 2017/tcp masquerade: no forward-ports: icmp-blocks: rich rules: [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=IT --list-all IT (active) interfaces: lo.0 sources: 192.168.254.1 services: ftp http ports: 2017/tcp masquerade: no forward-ports: icmp-blocks: rich rules: |
3. Essential 3 : Memanfaatkan fitur Masquerade Untuk NAT Internet
|
1 2 3 4 5 6 |
[root@Centos-FW ~]# firewall-cmd --zone=public --add-masquerade --permanent success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=public --list-all | grep masquerade masquerade: yes |
Jika anda ingin menghapusnya, lakukan langkah seperti berikut:
|
1 2 3 4 |
[root@Centos-FW ~]# firewall-cmd --zone=public --remove-masquerade --permanent success [root@Centos-FW ~]# firewall-cmd --reload success |
Dari host internal atau DMZ pastikan anda bisa akses internet 🙂 cukup simple ya haha
4. Essential 4 : Port Forwarding
Dengan firewalld ini bisa melakukan port-forwarding, sebagai contoh saat anda akses port 1000 maka nanti akan di forwarding ke port 2000 misalnya, kita juga melakukan set spesfik ip forwarding mau di arahin kemana, bisa saja anda forwarding ke local server itu sendiri, atau misal dari gateway Centos-FW anda forwarding ke server DMZ. Hal itu bisa saja anda lakukan tergantung kebutuhan anda.
|
1 2 3 4 |
[root@Centos-FW ~]# firewall-cmd --permanent --zone=public --add-forward-port=port=1222:proto=tcp:toport=22:toaddr=10.10.10.2 success [root@Centos-FW ~]# firewall-cmd --reload success |
Diatas adalah contoh setting port forwarding, misal dari public zone or internet anda akses port 1222 maka akan diterusin ke port 22 dengan ip address 10.10.10.2 untuk ip dmz nya. Untuk mengecek hasilnya lakukan step berikut:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
[root@Centos-FW ~]# firewall-cmd --zone=public --list-all public (default, active) interfaces: eno16777736 sources: services: dhcpv6-client dns ftp http https ssh telnet ports: 4500/tcp 500/udp 4500/udp masquerade: yes forward-ports: port=8080:proto=tcp:toport=80:toaddr=172.16.0.2 port=1222:proto=tcp:toport=22:toaddr=10.10.10.2 port=1122:proto=tcp:toport=22:toaddr=172.16.0.2 port=8443:proto=tcp:toport=443:toaddr=172.16.0.2 port=1022:proto=tcp:toport=22:toaddr=192.168.254.132 |
Forwarding port dari zone internal ke server dmz
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
[root@Centos-FW ~]# firewall-cmd --zone=internal --add-forward-port=port=2022:proto=tcp:toport=22:toaddr=10.10.10.2 --permanent success [root@Centos-FW ~]# firewall-cmd --reload success [root@Centos-FW ~]# firewall-cmd --zone=internal --list-all internal (active) interfaces: eno50332208 sources: services: dns ftp http ssh ports: 2022/tcp masquerade: no forward-ports: port=2022:proto=tcp:toport=22:toaddr=10.10.10.2 icmp-blocks: rich rules: |
Testing dari internal client ke dmz:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
root@my-macbook:/home/bunyamin# ssh root@172.16.0.1 -p 2022 root@172.16.0.1's password: Last login: Mon Jan 9 11:36:45 2017 from 172.16.0.2 [root@server01 ~]# [root@server01 ~]# ifconfig eno16777736 eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 10.10.10.2 netmask 255.255.255.0 broadcast 10.10.10.255 inet6 fe80::20c:29ff:fe16:1c1d prefixlen 64 scopeid 0x20<link> ether 00:0c:29:16:1c:1d txqueuelen 1000 (Ethernet) RX packets 14921 bytes 20090670 (19.1 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 6845 bytes 556368 (543.3 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
Oke cukup sampe dsini mengenai firewalld, jika ada pertanyaan lebih lanjut bisa langsung comment dibawah 🙂
Komentar