Post Views:
3,644
judulnya itu loh hoho….jadi ini artikel ingin membahas semua tentang si zones tapi bukan bang jones yang jauh disana yak hahaha :P. Semoga tulisan ini memberikan pengertian yang mendalam terkait apa itu zone pada juniper SRX? berikut ane kutip dari juniper.net;
A zone is a collection of one or more network segments sharing identical security requirements. To group network segments within a zone, you must assign logical interfaces from the device to a zone.
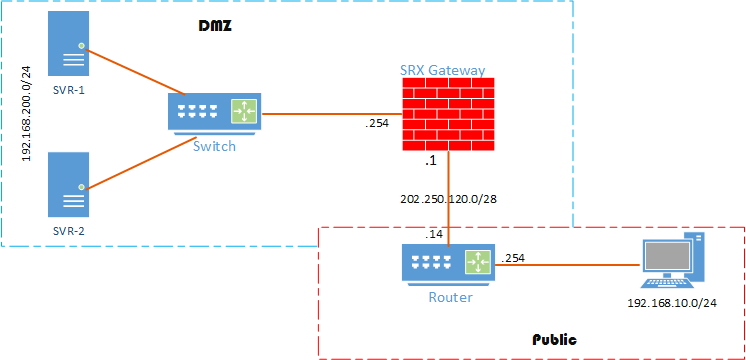
Jadi zone bisa disebut sebagai sebuah atau sekumpulan dari segment network yang memiliki ketentuan atau requerement yang sama. Sebagai contoh anda memiliki beberapa server maka anda mengelompokkan ke dalam zone Server atau DMZ, terus user-user yang akan menggunakan layanan server anda tentu berbeda dengan server yang anda miliki, dan anda mempertimbangkan tidak ingin server anda menyatu dengan jaringan user2, maka anda bisa memisahkan dengan zone User misalnya, dan seterusnya.. Jadi zone ini berfungsi memisahkan network yang ingin anda proteksi dari segmen network lain. Jika anda berpikir, bagaimana cara melakukannya? Silahkan ikutti langkah berikut:
- Define zone (security or functional)
- Add logical interfaces to the zone
- Define permitted services (example: Telnet, SSH) and protocols (example: OSPF) destined to device itself.
So,,. anda sudah tahu apa yang harus anda lakukan? Jadi diatas setidaknya ada tiga langkah ya untuk membuat zone, untuk zone itu sendiri ada security zone yaitu zone yang memang untuk mengidentifikasi flow traffic, sedangkan functional zone adalah zone khusus management srx, misal untuk remote srx anda bisa melakukan via interface yang di set sebagai functional atau management zone. Selanjutnya di dalam zone anda perlu menambahkan interface yang dari awal sudah anda identifikasi. Misal interface yang terkoneksi dengan server2, anda bisa memasukkan ke zone DMZ yang sudah anda buat. Langkah selanjutnya adalah mendefinisikan permit service seperti ssh, ping, atau ospf. Service ini bukan untuk mempermit traffic dari zone satu ke zone yang lain, akan tetapi service yang diizinkan dari host2 zone terkait ke interface SRX itu sendiri.
Oke, mari kita lihat detail satu persatu di SRX.
|
|
root# set security zones ? Possible completions: + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups > functional-zone Functional zone > security-zone Security zones [edit] |
jadi zone ada dua ya functional-zone, coba kita cek opsi selanjutnya.
|
|
root# set security zones functional-zone ? Possible completions: > management Host for out of band management interfaces [edit] |
nama zone sudah di define ya yaitu management zone,
|
|
root# set security zones functional-zone management ? Possible completions: <[Enter]> Execute this command + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups description Text description of zone > host-inbound-traffic Allowed system services & protocols > interfaces Interfaces that are part of this zone screen Name of ids option object applied to the zone | Pipe through a command [edit] |
seperti yang sudah dijelaskan seblumnya, bahwa di zone itu anda perlu menambah logical interface, yaitu di opsi interface, kemudian mempermit traffic yang ke SRX via interface tersebut pada opsi host-inbound-traffic. Mari kita lanjut ke opsi security zone.
|
|
root# set security zones security-zone ? Possible completions: <name> Name of the zone [edit] |
oke, coba anda buat security zone baru, misal DMZ.
|
|
root# set security zones security-zone DMZ ? Possible completions: <[Enter]> Execute this command > address-book Address book entries application-tracking Enable Application tracking support for this zone + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups description Text description of zone > host-inbound-traffic Allowed system services & protocols > interfaces Interfaces that are part of this zone screen Name of ids option object applied to the zone tcp-rst Send RST for NON-SYN packet not matching TCP session | Pipe through a command [edit] |
anda perlu menambah interface baru, pilih opsi interface di zone DMZ
|
|
root# set security zones security-zone DMZ interfaces ? Possible completions: <interface-unit> Logical interface ge-0/0/0 ge-0/0/1 ge-0/0/2 [edit] |
Oke, langkah selanjutnya anda bisa mempermit service di zone DMZ bisa langsung under zone DMZ atau under interface. seperti berikut:
|
|
root# ...rity-zone DMZ interfaces ge-0/0/2.0 host-inbound-traffic ? Possible completions: + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups > protocols Protocol type of incoming traffic to accept > system-services Type of incoming system-service traffic to accept [edit] root# ...rity-zone DMZ interfaces ge-0/0/2.0 host-inbound-traffic |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
root# ...aces ge-0/0/2.0 host-inbound-traffic system-services ? Possible completions: all All system services any-service Enable services on entire port range bootp Bootp and dhcp relay-agent service dhcp Dynamic Host Configuration Protocol dhcpv6 Enable Dynamic Host Configuration Protocol for IPv6 dns DNS service finger Finger service ftp FTP http Web management service using HTTP https Web management service using HTTP secured by SSL ident-reset Send back TCP RST to IDENT request for port 113 ike Internet Key Exchange lsping Label Switched Path ping service netconf NETCONF service ntp Network Time Protocol service ping Internet Control Message Protocol echo requests r2cp Enable Radio-Router Control Protocol service reverse-ssh Reverse SSH service reverse-telnet Reverse telnet service rlogin Rlogin service rpm Real-time performance monitoring rsh Rsh service sip Enable Session Initiation Protocol service snmp Simple Network Management Protocol service snmp-trap Simple Network Management Protocol traps ssh SSH service telnet Telnet service tftp TFTP traceroute Traceroute service xnm-clear-text JUNOScript API for unencrypted traffic over TCP xnm-ssl JUNOScript API service over SSL |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
root# ...aces ge-0/0/2.0 host-inbound-traffic protocols ? Possible completions: all All protocols bfd Bidirectional Forwarding Detection bgp Border Gateway Protocol dvmrp Distance Vector Multicast Routing Protocol igmp Internet Group Management Protocol ldp Label Distribution Protocol msdp Multicast Source Discovery Protocol nhrp Next Hop Resolution Protocol ospf Open Shortest Path First ospf3 Open Shortest Path First version 3 pgm Pragmatic General Multicast pim Protocol Independent Multicast rip Routing Information Protocol ripng Routing Information Protocol next generation router-discovery Router Discovery rsvp Resource Reservation Protocol sap Session Announcement Protocol vrrp Virtual Router Redundancy Protocol [edit] |
jadi, jika anda menggunakan routing protokol di interface tersebut, maka anda bisa melakukannya di opsi protocol. dan jika anda melakukkannya under interface maka services tersebut hanya berlaku di interface tersebut. jadi jika ada interface yang lain maka itu tidak berlaku. mari kita lihat contoh hasilnya.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
root# show security zones | display set set security zones security-zone DMZ interfaces ge-0/0/2.0 host-inbound-traffic system-services ping set security zones security-zone DMZ interfaces ge-0/0/2.0 host-inbound-traffic system-services dhcp set security zones security-zone DMZ interfaces ge-0/0/2.0 host-inbound-traffic protocols ospf set security zones security-zone DMZ interfaces ge-0/0/1.0 [edit] root# show security zones security-zone DMZ { interfaces { ge-0/0/2.0 { host-inbound-traffic { system-services { ping; dhcp; } protocols { ospf; } } } ge-0/0/1.0; } } [edit] |
nah, bisa anda lihat, contoh di atas, ge-0/0/2.0 memiliki service yang dibolehkan ping, dhcp, dan ospf. sedangkan ge-0/0/1.0 belum ada. Lalu apakah ge-0/0/1.0 sperti ini bermasalah? sebetulnya ini tidak masalah. hanya saja bila interface tersebut disambungkan ke komputer anda, maka anda tidak bisa melakukan apa2 untuk interface tersebut, misal ping, telnet atau lainnya. Oke ada gambaran ya..hehe.. Lalu bagaiamana jika anda melakukannya permit service under zone DMZ
|
|
root# set security zones security-zone DMZ host-inbound-traffic ? Possible completions: + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups > protocols Protocol type of incoming traffic to accept > system-services Type of incoming system-service traffic to accept [edit] |
Contoh hasilnya.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
set security zones security-zone DMZ host-inbound-traffic system-services all set security zones security-zone DMZ host-inbound-traffic protocols all Hasilnya: root# show security zones security-zone DMZ { host-inbound-traffic { system-services { all; } protocols { all; } } interfaces { ge-0/0/2.0 { host-inbound-traffic { system-services { ping; dhcp; } protocols { ospf; } } } ge-0/0/1.0; } } [edit] |
coba anda perhatikan, under zone DMZ di set protocol all system service all. Jika sperti diatas, maka ge-0/0/1.0 service nya all, sedangkan ge-0/0/2.0 tetap seperti yang diset atau yang ane sampaikan sebelumnya.
Untuk melihat hasilnya,silahkan di commit dan coba anda cek di mode operational
|
|
root> show security zones Security zone: DMZ Send reset for non-SYN session TCP packets: Off Policy configurable: Yes Interfaces bound: 2 Interfaces: ge-0/0/1.0 ge-0/0/2.0 |
lakukan show interface untuk lebih detailnya
|
|
root> show interfaces ge-0/0/1.0 Logical interface ge-0/0/1.0 (Index 70) (SNMP ifIndex 519) Flags: SNMP-Traps 0x4000 Encapsulation: ENET2 Input packets : 217 Output packets: 109 Security: Zone: DMZ Allowed host-inbound traffic : bootp bfd bgp dns dvmrp igmp ldp msdp nhrp ospf pgm pim rip router-discovery rsvp sap vrrp dhcp finger ftp tftp ident-reset http https ike netconf ping reverse-telnet reverse-ssh rlogin rpm rsh snmp snmp-trap ssh telnet traceroute xnm-clear-text xnm-ssl lsping ntp sip r2cp Protocol inet, MTU: 1500 Flags: Sendbcast-pkt-to-re Addresses, Flags: Is-Preferred Is-Primary Destination: 172.31.10/24, Local: 172.31.10.1, Broadcast: 172.31.10.255 |
|
|
root> show interfaces ge-0/0/2.0 Logical interface ge-0/0/2.0 (Index 74) (SNMP ifIndex 520) Flags: SNMP-Traps 0x4000 Encapsulation: ENET2 Input packets : 0 Output packets: 1 Security: Zone: DMZ Allowed host-inbound traffic : ospf dhcp ping Protocol inet, MTU: 1500 Flags: Sendbcast-pkt-to-re Addresses, Flags: Is-Preferred Is-Primary Destination: 10.0.0/24, Local: 10.0.0.1, Broadcast: 10.0.0.255 |
Oke, ane rasa sudah cukup jelas ya, jika ada pertanyaan silahkan comment dibawah 🙂
Komentar