Dear Juniper Customers,
Buat anda yang lagi bingung bagaimana cara update IPS juniper secara offline, nah tulisan ini saya rasa anda bisa ikuti dengan mudah. Sebetulnya juniper sudah banyak membuat dokumentasi cara update security package juniper srx secara offline, offline update template ips, offline update ips juniper srx cluster dan lain-lain. salah satunya yang paling lengkap dapat anda buka di link ini, Tulisan ini juga mengacau ke dokument tersebut dan saya juga menyarankan anda membaca dokument tersebut dari awal sampai akhir hehehe. Jadi tulisan ini menggunakan perangkat juniper SRX5800 cluster dengan junos version 12.3X48-D30.7. Mari kita ikuti langkah2 berikut:
Langkah 1: Download SignatureUpdate.xml.gz
langkah pertama anda perlu download file SignatureUpdate.xml.gz, ini adalah cara untuk download file signature ips yang paling update nantinya.
https://signatures.juniper.net/cgi-bin/index.cgi?device=srx5800&feature=idp&detector=12.6.140171124&to=latest&os=12.3&build=48&type=update
contoh di atas untuk srx5800 dengan junos 12.3X48-D30.7. jika anda memiliki seri branch maka silakan anda sesuaikan. detailnya berikut ini:
Note:
In the above URL we can observe the following:
For SRX highend device the device names are device=srx3400, srx3600 and so on
For SRX Branch devices the device names are device=jsrx210, jsrx240 and so on
For vSRX the device name is device=firefly-perimeter
os= indicates the SRX JunOS version currently installed from= current downloaded version (if there is no DB it will be null)
to = latest indicates download the latest security package. If not mentioned latest is downloaded
feature = idp (while other values above change – feature never changes)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
<?xml version='1.0' encoding='UTF-8'?> <SignatureUpdate type="base"> <XMLVersion>1.0.0</XMLVersion> <UpdateNumber>3064</UpdateNumber> <ExportDate>Thu May 10 11:06:22 2018 UTC</ExportDate> <ApplicationGroups md5="4a41b30cc1cf40b983a27bf87e61e740" version="3064">https://signatures.juniper.net/xmlupdate/225/ApplicationGroups/3064/application_groups.xml.gz</ApplicationGroups> <ApplicationGroups2 md5="dc99661338597dd8e72582a11cb4a10e" version="3064">https://signatures.juniper.net/xmlupdate/225/ApplicationGroups/3064/application_groups2.xml.gz</ApplicationGroups2> <ApplicationSchema md5="b309c781a484fcb3a03b8f1ad3c81a8e" version="3064">https://signatures.juniper.net/xmlupdate/225/Applications/3064/applications.xsd</ApplicationSchema> <Applications md5="8522507b20f1b8b984c812dadc068262" version="3064">https://signatures.juniper.net/xmlupdate/225/Applications/3064/applications.xml.gz</Applications> <Applications2 md5="5de1d7e35100eb6d74acbcd818c36e0f" version="3064">https://signatures.juniper.net/xmlupdate/225/Applications/3064/applications2.xml.gz</Applications2> <Contexts md5="f867e2d7df0191e9318a44d249ddd46a" version="3064">https://signatures.juniper.net/xmlupdate/225/Contexts/3064/contexts.xml.gz</Contexts> <Detector md5="b5cdb643ef48a1c714b9b94082e5b93a" version="12.6.140171124" family="srx">https://signatures.juniper.net/xmlupdate/225/Detector/12.6.140171124/libidp-detector.so.tgz.v</Detector> <Filters md5="e71a2726ab5e1bb32557e9d9f49ebfec" version="3064">https://signatures.juniper.net/xmlupdate/225/Filters/3064/filters.xml.gz</Filters> <Groups md5="be795e82cebf262eb46f20fb8e432826" version="3064">https://signatures.juniper.net/xmlupdate/225/Groups/3064/groups.xml.gz</Groups> <Heuristics md5="4db1e6edb167591386fdb6a6a4694b0a" version="3064">https://signatures.juniper.net/xmlupdate/225/Heuristics/3064/heuristics.bin.gz</Heuristics> <Libqmprotocols md5="f0c32a0dd8aee83a8166b4c303d711e3" version="1.340.0-57.005" buildtime="Apr 19 2018 00:32:34" engine_version="4.20.0-87.005">https://signatures.juniper.net/xmlupdate/225/Libqmprotocols/1.340.0-57.005/libqmprotocols.tgz</Libqmprotocols> <Platforms md5="9ed461282cf9b9f134c0b5350c8f6b94" version="3064">https://signatures.juniper.net/xmlupdate/225/Platforms/3064/platforms.xml.gz</Platforms> <Products md5="617c15295445479742f463b4c13244b5" version="3064">https://signatures.juniper.net/xmlupdate/225/Products/3064/products.xml.gz</Products> <Services md5="178c8dbaa4709e888b98965d7350a32a" version="3064">https://signatures.juniper.net/xmlupdate/225/Services/3064/services.xml.gz</Services> <Templates md5="8fa1f262cd30c8bc036b789cbef63a93" version="3064">https://signatures.juniper.net/xmlupdate/225/Templates/3064/templates.xml.gz</Templates> <Entries> <Entry> [output cut] |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 |
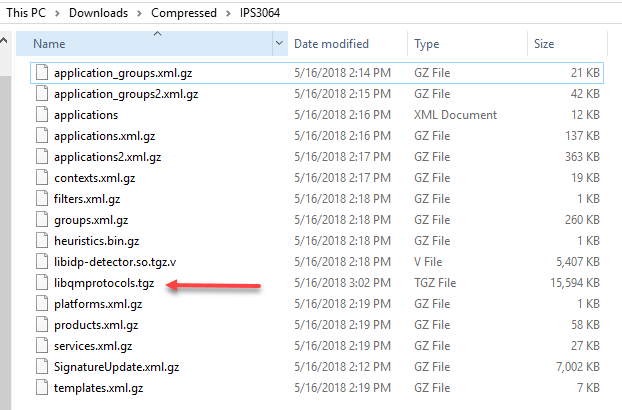
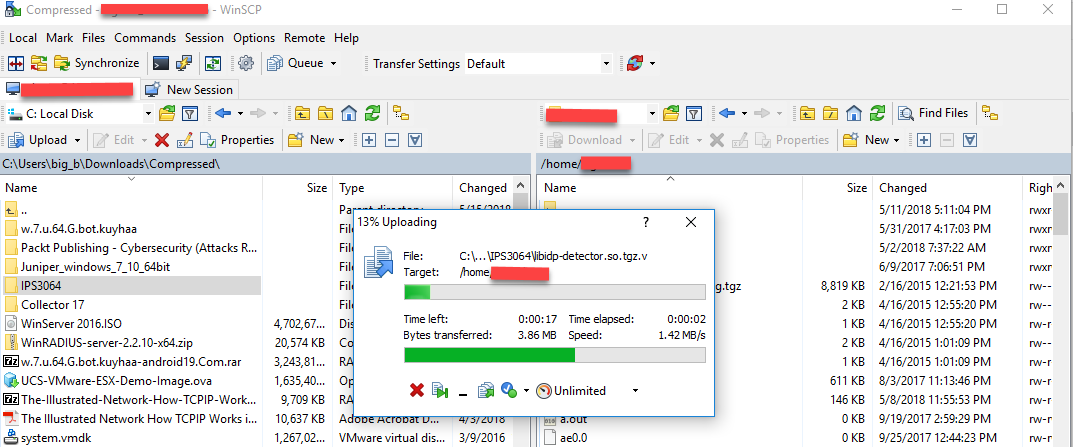
user@SRX-1% sftp user@192.168.1.2 Verification code: Password: Connected to 192.168.1.2. sftp> pwd Remote working directory: /home/user sftp> cd IPS3064/ sftp> ls application_groups.xml.gz libqmprotocols.tar application_groups2.xml.gz heuristics.bin.gz applications.xml contexts.xml.gz platforms.xml.gz groups.xml.gz applications.xml.gz filters.xml.gz products.xml.gz applications2.xml.gz libidp-detector.so.tgz.v services.xml.gz SignatureUpdate.xml.gz templates.xml.gz sftp> get * sftp> bye user@SRX-1% gzip -d nama_file(kecuali file libqmprotocols.tgz jangan di gzip) user@SRX-1% ls -al total 209476 drwxr-xr-x 3 root wheel 512 May 16 16:37 . drwxr-xr-x 8 root wheel 512 May 16 16:39 .. -rw-r--r-- 1 root wheel 69449024 May 16 14:38 SignatureUpdate.xml -rw-r--r-- 1 root wheel 315957 May 16 14:38 application_groups.xml -rw-r--r-- 1 root wheel 584586 May 16 14:38 application_groups2.xml -rw-r--r-- 1 root wheel 2181027 May 16 14:38 applications.xml -rw-r--r-- 1 root wheel 5187079 May 16 14:38 applications2.xml -rw-r--r-- 1 root wheel 293017 May 16 14:38 contexts.xml -rwxr-xr-x 1 root wheel 762985 May 16 16:39 detector-capabilities.xml -rw-r--r-- 1 root wheel 5232 May 16 14:38 filters.xml -rw-r--r-- 1 root wheel 5045870 May 16 14:38 groups.xml -rw-r--r-- 1 root wheel 14545 May 16 14:38 heuristics.bin -rw-r--r-- 1 root wheel 5536491 May 16 14:38 libidp-detector.so.tgz.v -rw-r--r-- 1 root wheel 15968207 May 16 16:23 libqmprotocols.tgz -rw-r--r-- 1 root wheel 83 May 16 16:24 manifest.xml -rw-r--r-- 1 root wheel 492 May 16 14:38 platforms.xml -rw-r--r-- 1 root wheel 562054 May 16 14:38 products.xml -rw-r--r-- 1 root wheel 854005 May 16 14:38 services.xml drwxr-xr-x 2 root wheel 512 May 16 14:39 sub-download -rw-r--r-- 1 root wheel 165525 May 16 14:38 templates.xml user@SRX-1% pwd /var/db/idpd/sec-download user@SRX-1% cp SignatureUpdate.xml /var/db/idpd/sec-download/sub-download/ user@SRX-1% cp templates.xml /var/db/idpd/sec-download/sub-download/ user@SRX-1% ls sub-download/ SignatureUpdate.xml templates.xml |
f. jika srx anda adalah cluster, maka semua isi folder sec-download perlu anda copy-kan juga ke node satu nya lagi. stepnya seperti berikut ini.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
user@SRX-2% rlogin -T node1 user@SRX-2% cd /var/db/idpd/sec-download/ user@SRX-2% ls SignatureUpdate.xml groups.xml application_groups.xml libidp-detector.so.tgz.v application_groups2.xml libqmprotocols.tar applications.xml platforms.xml applications.xsd products.xml applications2.xml services.xml contexts.xml sub-download detector-capabilities.xml templates.xml filters.xml root@SRX-2% rm * rm: sub-download: is a directory user@SRX-2% cd sub-download/ user@SRX-2% ls SignatureUpdate.xml templates.xml user@SRX-2% rm * user@SRX-2% ls user@SRX-2% |
anda sudah membersihkan isi folder sec-download di SRX-2. maka anda skrng balik ke SRX-1 lagi,
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
user@SRX-2% exit logout rlogin: connection closed user@SRX-1% root@SRX-1-GI-TBS% rcp -r -T /var/db/idpd/sec-download/* node1:/var/db/idpd/sec-download/ user@SRX-2% rlogin -T node1 user@SRX-2% pwd /cf/root user@SRX-2% cd /var/db/idpd/sec-download/ user@SRX-2% ls SignatureUpdate.xml applications2.xml groups.xml manifest.xml sub-download application_groups.xml contexts.xml heuristics.bin platforms.xml templates.xml application_groups2.xml detector-capabilities.xml libidp-detector.so.tgz.v products.xml applications.xml filters.xml libqmprotocols.tgz services.xml user@SRX-2% exit logout rlogin: connection closed user@SRX-1% |
jadi jika anda cek di SRX-2 lagi, filenya sudah berhasil anda copy dari SRX-1 ke SRX-2.
Langkah 4: Install security package di SRX
Pada case ini sy lakukan di srx cluster,
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
root@SRX-2> request security idp security-package install source-path /var/db/idpd/sec-download node 1 node1: -------------------------------------------------------------------------- Will be processed in async mode. Check the status using the status checking CLI root@SRX-2> request security idp security-package install status node 1 node1: -------------------------------------------------------------------------- In progress:Installing AI ... root@SRX-2> request security idp security-package install status node 1 node1: -------------------------------------------------------------------------- In progress:performing DB update for an xml (SignatureUpdate.xml) root@SRX-2> request security idp security-package install status node 1 node1: -------------------------------------------------------------------------- Done;Attack DB update : successful - [UpdateNumber=3064,ExportDate=Thu May 10 11:06:22 2018 UTC,Detector=12.6.140171124] Updating control-plane with new detector : successful Updating data-plane with new attack or detector : successful |
Lakukan juga pada SRX-1
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
user@SRX-1> request security idp security-package install source-path /var/db/idpd/sec-download node 1 node1: -------------------------------------------------------------------------- Will be processed in async mode. Check the status using the status checking CLI user@SRX-1> request security idp security-package install status node 0 node0: -------------------------------------------------------------------------- In progress:performing DB update for an xml (SignatureUpdate.xml) user@SRX-2> request security idp security-package install status node 0 node0: -------------------------------------------------------------------------- Done;Attack DB update : successful - [UpdateNumber=3064,ExportDate=Thu May 10 11:06:22 2018 UTC,Detector=12.6.140171124] Updating control-plane with new detector : successful Updating data-plane with new attack or detector : successful |
Cek hasil akhir:
Capture sebelum update:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
root@SRX-1> show security idp security-package-version node0: -------------------------------------------------------------------------- Attack database version:3047(2018-03-21 17:18:12) Detector version :12.6.140171124 Policy template version :2879 node1: -------------------------------------------------------------------------- Attack database version:3047(2018-03-21 17:18:12) Detector version :12.6.140171124 Policy template version :N/A |
Capture setelah update:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
root@SRX-1> show security idp security-package-version node0: -------------------------------------------------------------------------- Attack database version:3064(Thu May 10 11:06:22 2018 UTC) Detector version :12.6.140171124 Policy template version :2879 node1: -------------------------------------------------------------------------- Attack database version:3064(Thu May 10 11:06:22 2018 UTC) Detector version :12.6.140171124 Policy template version :N/A |
Demikian tulisan terkait cara update ips juniper srx, smoga bermanfaat buat customer juniper 🙂
Komentar