Bagian ini perlu saya tulis, karena ini adalah salah part yang cukup penting dan banyak kebutuhan yang membutuhkan koneksi vpn. Perlu diketahui di juniper ada ada dua macam site-to-site (s2s), yaitu route based vpn dan policy based vpn. Beda nya apa? jadi klo policy based vpn itu untuk kebutuhan jika site remote adalah platform yang berbeda, sama yang kedua adalah jika ada hanya satu client atau satu subnet yang terkoneksi. Nah jadi jika ada design yang complex kira2, misalanya vpn hub-and-spoko, or site remote nya banyak, maka itu membutuhkan route based vpn, jiak nanti membutuhkan implementas nat, menghindari overlapping address, terus menggunakan dynamic routing procotol, ini juga harus menggunakan route based vpn. Jadi pada kesempatan ini kita akan coba setup route-based s2s vpn dengan konfigurasi dan design standar.
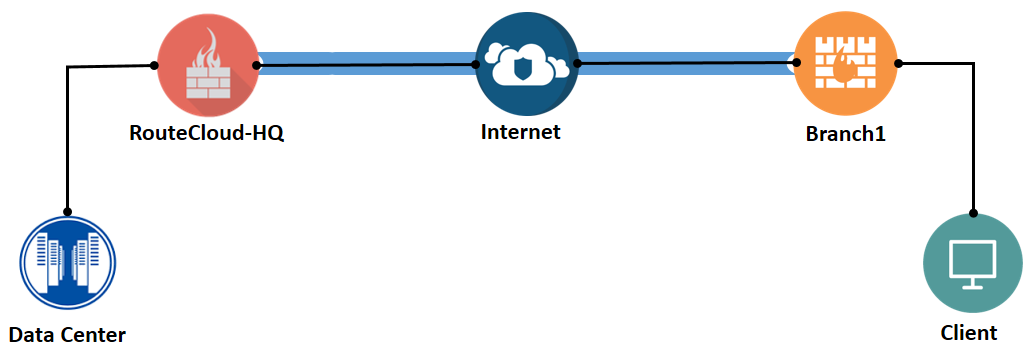
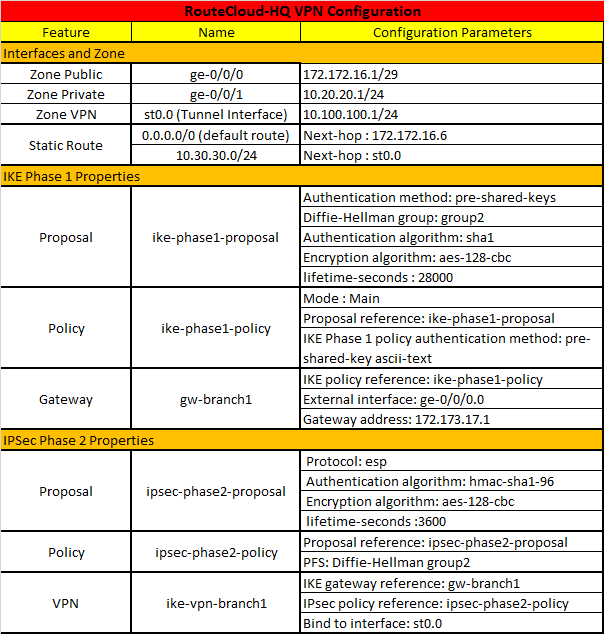
Ini adalah contoh design yang nanti akan kita konfigurasi, RouteCloud-HQ dan Branch1, keduanya menggunakan platform juniper SRX. Mari kita lihat tabel konfigurasi SRX untuk masing-masing site nya.
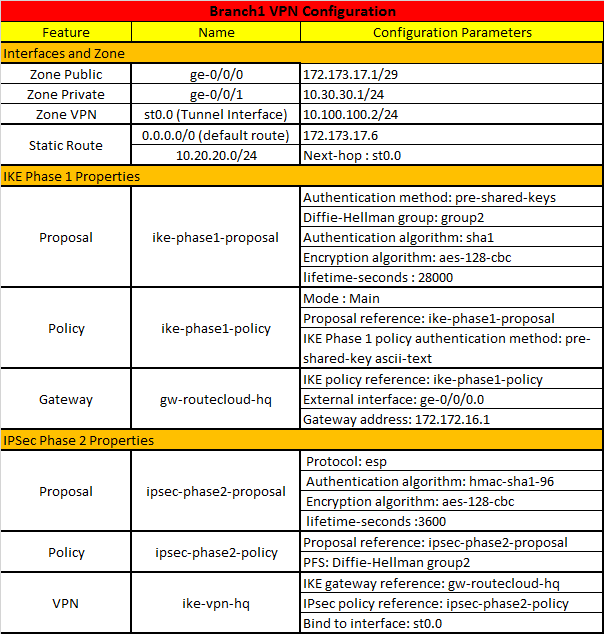
Kemudian yang kedua adalah konfigurasi untuk SRX Branch1
Jika anda perhatikan table di atas, maka anda seharusnya sudah tau parameter apa saja yang perlu di configure.
#RouteCloud-HQ
Interface Configuration, Zone, Routing Static, Rule-policy
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
set interfaces ge-0/0/0 unit 0 family inet address 172.172.16.1/29 set interfaces ge-0/0/1 unit 0 family inet address 10.20.20.1/24 set interfaces st0 unit 0 point-to-point set interfaces st0 unit 0 family inet address 10.100.100.1/24 set security zones security-zone Public interfaces ge-0/0/0.0 host-inbound-traffic system-services ike set security zones security-zone Public interfaces ge-0/0/0.0 host-inbound-traffic system-services ping set security zones security-zone Private interfaces ge-0/0/1.0 host-inbound-traffic system-services all set security zones security-zone Private interfaces ge-0/0/1.0 host-inbound-traffic protocols all set security zones security-zone VPN interfaces st0.0 host-inbound-traffic system-services ping set routing-options static route 10.30.30.0/24 next-hop st0.0 set routing-options static route 0.0.0.0/0 next-hop 172.172.16.6 set security policies from-zone Private to-zone VPN policy permit-private-vpn match source-address any set security policies from-zone Private to-zone VPN policy permit-private-vpn match destination-address any set security policies from-zone Private to-zone VPN policy permit-private-vpn match application any set security policies from-zone Private to-zone VPN policy permit-private-vpn then permit set security policies from-zone VPN to-zone Private policy permit-private-vpn match source-address any set security policies from-zone VPN to-zone Private policy permit-private-vpn match destination-address any set security policies from-zone VPN to-zone Private policy permit-private-vpn match application any set security policies from-zone VPN to-zone Private policy permit-private-vpn then permit |
IKE Phase 1 Configuration:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
set security ike proposal ike-phase1-proposal authentication-method pre-shared-keys set security ike proposal ike-phase1-proposal dh-group group2 set security ike proposal ike-phase1-proposal authentication-algorithm sha1 set security ike proposal ike-phase1-proposal encryption-algorithm aes-128-cbc set security ike proposal ike-phase1-proposal lifetime-seconds 28000 set security ike policy ike-phase1-policy mode main set security ike policy ike-phase1-policy proposals ike-phase1-proposal set security ike policy ike-phase1-policy pre-shared-key ascii-text "bunyamin123" set security ike gateway gw-branch1 ike-policy ike-phase1-policy set security ike gateway gw-branch1 address 172.173.17.1 set security ike gateway gw-branch1 external-interface ge-0/0/0 |
IPSec Phase 2 Configuration:
|
1 2 3 4 5 6 7 8 9 10 11 |
set security ipsec proposal ipsec-phase2-proposal protocol esp set security ipsec proposal ipsec-phase2-proposal authentication-algorithm hmac-sha1-96 set security ipsec proposal ipsec-phase2-proposal encryption-algorithm aes-128-cbc set security ipsec proposal ipsec-phase2-proposal lifetime-seconds 3600 set security ipsec policy ipsec-phase2-policy perfect-forward-secrecy keys group2 set security ipsec policy ipsec-phase2-policy proposals ipsec-phase2-proposal set security ipsec vpn ike-vpn-branch1 bind-interface st0.0 set security ipsec vpn ike-vpn-branch1 ike gateway gw-branch1 set security ipsec vpn ike-vpn-branch1 ike ipsec-policy ipsec-phase2-policy |
#Branch Configuration
Interface Configuration, Zone, Routing Static, Rule-policy
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
set interfaces ge-0/0/0 unit 0 family inet address 172.173.17.1/29 set interfaces ge-0/0/1 unit 0 family inet address 10.30.30.1/24 set interfaces st0 unit 0 point-to-point set interfaces st0 unit 0 family inet address 10.100.100.2/24 set security zones security-zone Public interfaces ge-0/0/0.0 host-inbound-traffic system-services ike set security zones security-zone Public interfaces ge-0/0/0.0 host-inbound-traffic system-services ping set security zones security-zone Private interfaces ge-0/0/1.0 host-inbound-traffic system-services all set security zones security-zone Private interfaces ge-0/0/1.0 host-inbound-traffic protocols all set security zones security-zone VPN interfaces st0.0 host-inbound-traffic system-services ping set routing-options static route 0.0.0.0/0 next-hop 172.173.17.6 set routing-options static route 10.20.20.0/24 next-hop st0.0 set security policies from-zone Private to-zone VPN policy permit-private-vpn match source-address any set security policies from-zone Private to-zone VPN policy permit-private-vpn match destination-address any set security policies from-zone Private to-zone VPN policy permit-private-vpn match application any set security policies from-zone Private to-zone VPN policy permit-private-vpn then permit set security policies from-zone VPN to-zone Private policy permit-private-vpn match source-address any set security policies from-zone VPN to-zone Private policy permit-private-vpn match destination-address any set security policies from-zone VPN to-zone Private policy permit-private-vpn match application any set security policies from-zone VPN to-zone Private policy permit-private-vpn then permit |
IKE Phase 1 Configuration:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
set security ike proposal ike-phase1-proposal authentication-method pre-shared-keys set security ike proposal ike-phase1-proposal dh-group group2 set security ike proposal ike-phase1-proposal authentication-algorithm sha1 set security ike proposal ike-phase1-proposal encryption-algorithm aes-128-cbc set security ike proposal ike-phase1-proposal lifetime-seconds 28000 set security ike policy ike-phase1-policy mode main set security ike policy ike-phase1-policy proposals ike-phase1-proposal set security ike policy ike-phase1-policy pre-shared-key ascii-text "bunyamin123" set security ike gateway gw-routecloud-hq ike-policy ike-phase1-policy set security ike gateway gw-routecloud-hq address 172.172.16.1 set security ike gateway gw-routecloud-hq external-interface ge-0/0/0 |
IPSec Phase 2 Configuration:
|
1 2 3 4 5 6 7 8 9 10 11 |
set security ipsec proposal ipsec-phase2-proposal protocol esp set security ipsec proposal ipsec-phase2-proposal authentication-algorithm hmac-sha1-96 set security ipsec proposal ipsec-phase2-proposal encryption-algorithm aes-128-cbc set security ipsec proposal ipsec-phase2-proposal lifetime-seconds 3600 set security ipsec policy ipsec-phase2-policy perfect-forward-secrecy keys group2 set security ipsec policy ipsec-phase2-policy proposals ipsec-phase2-proposal set security ipsec vpn ike-vpn-hq bind-interface st0.0 set security ipsec vpn ike-vpn-hq ike gateway gw-routecloud-hq set security ipsec vpn ike-vpn-hq ike ipsec-policy ipsec-phase2-policy |
Testing dan Verification:
Pastikan ip-peer nya sama-sama bisa direach oleh masing2 site:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
root@Branch1> ping 172.172.16.1 PING 172.172.16.1 (172.172.16.1): 56 data bytes 64 bytes from 172.172.16.1: icmp_seq=0 ttl=62 time=52.095 ms 64 bytes from 172.172.16.1: icmp_seq=1 ttl=62 time=6.335 ms 64 bytes from 172.172.16.1: icmp_seq=2 ttl=62 time=147.276 ms ^C --- 172.172.16.1 ping statistics --- 3 packets transmitted, 3 packets received, 0% packet loss round-trip min/avg/max/stddev = 6.335/68.569/147.276/58.706 ms root@RouteCloud-HQ> ping 172.173.17.1 rapid count 10 PING 172.173.17.1 (172.173.17.1): 56 data bytes !!!!!!!!!! --- 172.173.17.1 ping statistics --- 10 packets transmitted, 10 packets received, 0% packet loss round-trip min/avg/max/stddev = 10.440/191.195/602.093/208.497 ms root@RouteCloud-HQ> |
Sekarang coba anda ping ip internal:
|
1 2 3 4 5 6 7 8 |
root@Branch1> ping 10.20.20.1 source 10.30.30.1 rapid count 10 PING 10.20.20.1 (10.20.20.1): 56 data bytes !!!!!!!!!! --- 10.20.20.1 ping statistics --- 10 packets transmitted, 10 packets received, 0% packet loss round-trip min/avg/max/stddev = 11.239/25.583/57.729/18.166 ms root@Branch1> |
Melihat status phase1 dan phase2:
|
1 2 3 4 5 6 7 8 9 |
root@Branch1> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 7296309 UP 6a3128a8da104fe2 707f732d5a216a95 Main 172.172.16.1 root@Branch1> show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <131075 ESP:aes-cbc-128/sha1 69bca620 2962/ unlim - root 500 172.172.16.1 >131075 ESP:aes-cbc-128/sha1 cd530f3a 2962/ unlim - root 500 172.172.16.1 |
Jika state UP pada phase1 maka itu menunjukkan kedua site sudah melakukan negosiasi dan sudah establish. Kemudian phase2 juga terbentuk, dengan active tunnel 1.
Melihat jumlah peering yang sedang active:
|
1 2 3 |
root@RouteCloud-HQ> show security ike active-peer Remote Address Port Peer IKE-ID XAUTH username Assigned IP 172.173.17.1 500 172.173.17.1 |
Melihat secara detail status phase1 dan phase2
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 |
root@RouteCloud-HQ> show security ike security-associations detail IKE peer 172.173.17.1, Index 6404394, Gateway Name: gw-branch1 Role: Responder, State: UP Initiator cookie: 6a3128a8da104fe2, Responder cookie: 707f732d5a216a95 Exchange type: Main, Authentication method: Pre-shared-keys Local: 172.172.16.1:500, Remote: 172.173.17.1:500 Lifetime: Expires in 26462 seconds Peer ike-id: 172.173.17.1 Xauth assigned IP: 0.0.0.0 Algorithms: Authentication : hmac-sha1-96 Encryption : aes128-cbc Pseudo random function: hmac-sha1 Diffie-Hellman group : DH-group-2 Traffic statistics: Input bytes : 1000 Output bytes : 796 Input packets: 5 Output packets: 4 Flags: IKE SA is created IPSec security associations: 1 created, 0 deleted Phase 2 negotiations in progress: 0 Negotiation type: Quick mode, Role: Responder, Message ID: 0 Local: 172.172.16.1:500, Remote: 172.173.17.1:500 Local identity: 172.172.16.1 Remote identity: 172.173.17.1 Flags: IKE SA is created root@RouteCloud-HQ> show security ipsec security-associations detail ID: 131074 Virtual-system: root, VPN Name: ike-vpn-branch1 Local Gateway: 172.172.16.1, Remote Gateway: 172.173.17.1 Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Version: IKEv1 DF-bit: clear Bind-interface: st0.0 Port: 500, Nego#: 2, Fail#: 0, Def-Del#: 0 Flag: 0x600a29 Last Tunnel Down Reason: Config Change Direction: inbound, SPI: cd530f3a, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 2044 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1456 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (128 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Direction: outbound, SPI: 69bca620, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 2044 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1456 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (128 bits) Anti-replay service: counter-based enabled, Replay window size: 64 |
Oke cukup sekian untuk pengenalan konfigurasi s2s vpn.
good luck 🙂
Komentar