I made this and this is a note for me as an engineer 🙂 #ea.. If you want to really understand about this post, take your time to understand some of my previous posting in this blog, start from basic is here, if you ready understand, now you can check other post about source nat and destination nat.
Oke done and you’re ready going to the next part 🙂
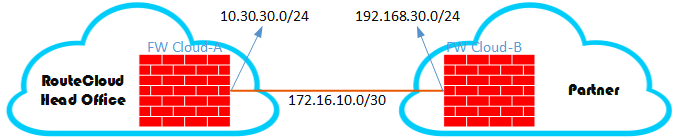
Baik, jika anda sudah mengerti maka anda boleh melanjutkan mengikuti tulisan ini, sekali lagi tulisan ini sbetulnya gabungan dari beberapa tulisan sebelumnya, yaitu tentang source nat, destination nat, ataupun static nat. Tulisan ini juga mengikuti kebutuhan di real network design and security, khususnya menggunakan firewall srx. atau anda yang baru ingin mamahami terkait hal ini, mungkin ini akan menjadi pertimbangan anda untuk selanjutnya. Mari kita lihat gambar berikut sapaya lebih clear hehe
Quick description: Jadi company RouteCloud Head Office memiliki mitra or partner. Jadi partner mereka ingin menghubungkan network mereka dengan network (service) routecloud. Mereka tidak menginginkan untuk share network, karena dengan alasan security, capacity, best practice atau yang lainnya. Jadi solusinya disini dengan menggunakan NAT salah satunya. Jadi nat dsini ada dua sisi inside dan outside di masing-masing firewall atau bahasa mudahnya di NAT dua kali.
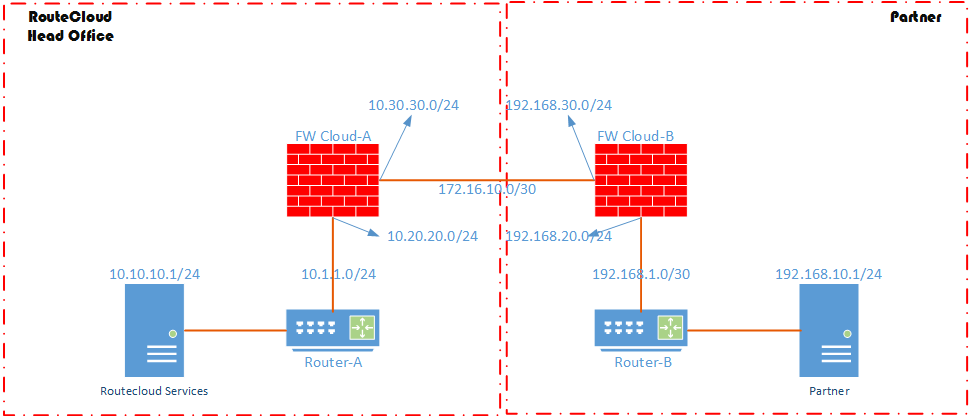
Contoh design diatas, tidak terlalu rumit dan pusing untuk diperhatikan. Disarankan anda hanya perlu fokus ke dua firewall yakni FW Cloud-A dan Cloud-B. In this case, Kedua cloud atau perusahaan tersebut, mareka hanya mengenal ip point-to-pint nya sama segmen nat antara firewall mereka. Mereka juga tidak mengetahui segmen nat untuk internal network mereka. Jika digambarkan lagi seperti inilah sederhananya.
Oke semoga anda mendapat gambaran yang cukup baik terkait apa yang ingin kita lakukan. Mari kita lihat detail step konfigurasi yang dilakukan:
Konfigurasi awal di sisi Partner:
Router-B
|
1 2 3 4 |
set interfaces em0 unit 0 description "LAN Partner" set interfaces em0 unit 0 family inet address 192.168.10.254/24 set interfaces em1 unit 0 description "P2P FW CLoud-B" set interfaces em1 unit 0 family inet address 192.168.1.2/30 |
|
1 |
set routing-options static route 192.168.20.0/24 next-hop 192.168.1.1 |
Diatas adalah static route ke arah ip pool internal Partner.
FW-CloudB
Berikut adalah config awal di firewall partner, config ini perlu supaya topology yang diinginkan terbentuk.
|
1 2 3 4 5 6 7 |
set interfaces ge-0/0/0 unit 0 family inet address 192.168.1.1/30 set interfaces ge-0/0/0 unit 0 family inet address 192.168.20.254/24 set interfaces ge-0/0/1 vlan-tagging set interfaces ge-0/0/1 unit 10 description "P2P TO ROUTECLOUD Head Office" set interfaces ge-0/0/1 unit 10 vlan-id 10 set interfaces ge-0/0/1 unit 10 family inet address 172.16.10.2/30 set interfaces ge-0/0/1 unit 10 family inet address 192.168.30.254/24 |
|
1 2 3 4 5 6 |
set security zones security-zone UNTRUST host-inbound-traffic system-services all set security zones security-zone UNTRUST host-inbound-traffic protocols all set security zones security-zone UNTRUST interfaces ge-0/0/1.10 set security zones security-zone TRUST host-inbound-traffic system-services all set security zones security-zone TRUST host-inbound-traffic protocols all set security zones security-zone TRUST interfaces ge-0/0/0.0 |
static route di fw partner hanya perlu diset ke ip pool routecloud 10.30.30.0/24 sama yang ke arah ip segmen lan partner itu sendiri, berikut detailnya.
|
1 2 |
set routing-options static route 10.30.30.0/24 next-hop 172.16.10.1 set routing-options static route 192.168.10.0/24 next-hop 192.168.1.2 |
Selanjutnya kita create rule policy, disni kita tidak fokus pada custom rule policy nya, maka dsini dibuat rule permit any saja.
|
1 2 3 4 |
set security policies from-zone TRUST to-zone UNTRUST policy PermitAll match source-address any set security policies from-zone TRUST to-zone UNTRUST policy PermitAll match destination-address any set security policies from-zone TRUST to-zone UNTRUST policy PermitAll match application any set security policies from-zone TRUST to-zone UNTRUST policy PermitAll then permit |
Konfigurasi awal disisi Route Cloud Head Office:
Router-A
Config interface:
|
1 2 3 4 |
set interfaces em0 unit 0 family inet address 10.10.10.254/24 set interfaces em1 vlan-tagging set interfaces em1 unit 1 vlan-id 1 set interfaces em1 unit 1 family inet address 10.1.1.2/30 |
Config routing, disni menggunakan config ospf standar.
|
1 2 |
set protocols ospf area 0.0.0.0 interface em0.0 set protocols ospf area 0.0.0.0 interface em1.1 |
Selanjutnya mari kita lihat config di firewall FW CloudA
|
1 2 3 4 5 6 7 8 9 10 |
set interfaces ge-0/0/0 vlan-tagging set interfaces ge-0/0/0 unit 1 description "P2P TO MX-80 DC" set interfaces ge-0/0/0 unit 1 vlan-id 1 set interfaces ge-0/0/0 unit 1 family inet address 10.1.1.1/30 set interfaces ge-0/0/0 unit 1 family inet address 10.20.20.254/24 set interfaces ge-0/0/1 vlan-tagging set interfaces ge-0/0/1 unit 10 description "P2P TO PARTNER-A" set interfaces ge-0/0/1 unit 10 vlan-id 10 set interfaces ge-0/0/1 unit 10 family inet address 172.16.10.1/30 set interfaces ge-0/0/1 unit 10 family inet address 10.30.30.254/24 |
|
1 2 |
root@FW.CloudA# show protocols | display set set protocols ospf area 0.0.0.0 interface ge-0/0/0.1 |
Diatas adalah config ospf, yang perlu di advertise ke ospf adalah interface yang ke arah network internal saja. Untuk network yang mengarah ke partner, disni menggunakan routing-instance or virtual routing forwarding (VRF). Jadi routing table nya di pisah antara internal network routecloud dengan route table yang mengarah ke partner.
|
1 2 3 4 5 |
root@FW.CloudA# show routing-instances PARTNER_A | display set set routing-instances PARTNER_A instance-type virtual-router set routing-instances PARTNER_A interface ge-0/0/1.10 set routing-instances PARTNER_A routing-options interface-routes rib-group inet Outside_to_Inside set routing-instances PARTNER_A routing-options static route 192.168.30.0/24 next-hop 172.16.10.2 |
sekarang buat rib group nya supaya route table Partner ke share juga di route table default inet.0, detail nya sbb:
|
1 2 3 4 5 6 7 |
[edit] root@FW.CloudA# show routing-options rib-groups { Outside_to_Inside { import-rib [ PARTNER_A.inet.0 inet.0 ]; } } |
Penasaran gimana jadinya? coba kita show route ya,
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
root@FW.CloudA# run show route table PARTNER_A.inet.0 PARTNER_A.inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 10.30.30.0/24 *[Direct/0] 04:20:26 > via ge-0/0/1.10 10.30.30.254/32 *[Local/0] 04:20:28 Local via ge-0/0/1.10 172.16.10.0/30 *[Direct/0] 04:20:26 > via ge-0/0/1.10 172.16.10.1/32 *[Local/0] 04:20:28 Local via ge-0/0/1.10 192.168.30.0/24 *[Static/5] 04:20:26 > to 172.16.10.2 via ge-0/0/1.10 |
Adapun route table di internal network routecloud adalah:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
root@FW.CloudA# run show route table inet.0 inet.0: 10 destinations, 10 routes (10 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 10.1.1.0/30 *[Direct/0] 04:22:35 > via ge-0/0/0.1 10.1.1.1/32 *[Local/0] 04:22:37 Local via ge-0/0/0.1 10.10.10.0/24 *[OSPF/10] 04:22:25, metric 2 > to 10.1.1.2 via ge-0/0/0.1 10.20.20.0/24 *[Direct/0] 04:22:35 > via ge-0/0/0.1 10.20.20.254/32 *[Local/0] 04:22:37 Local via ge-0/0/0.1 10.30.30.0/24 *[Direct/0] 04:22:35 > via ge-0/0/1.10 10.30.30.254/32 *[Local/0] 04:22:35 Local via ge-0/0/1.10 172.16.10.0/30 *[Direct/0] 04:22:35 > via ge-0/0/1.10 172.16.10.1/32 *[Local/0] 04:22:35 Local via ge-0/0/1.10 224.0.0.5/32 *[OSPF/10] 04:22:51, metric 1 MultiRecv |
Selanjutnya tidak perlu ada lagi routing yang perlu anda buat dari routecloud ke partner atau sebaliknya, ingat semuanya dilakukan dengan nat hehehe…Jangan lupa create zone dan rule policy, buat testing set policy nya permit any saja.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
root@FW.CloudA# show security zones | display set set security zones security-zone OUTSIDE host-inbound-traffic system-services all set security zones security-zone OUTSIDE host-inbound-traffic protocols all set security zones security-zone OUTSIDE interfaces ge-0/0/1.10 set security zones security-zone INSIDE host-inbound-traffic system-services all set security zones security-zone INSIDE host-inbound-traffic protocols all set security zones security-zone INSIDE interfaces ge-0/0/0.1 root@FW.CloudA# show security policies | display set set security policies from-zone INSIDE to-zone OUTSIDE policy PermitAll match source-address any set security policies from-zone INSIDE to-zone OUTSIDE policy PermitAll match destination-address any set security policies from-zone INSIDE to-zone OUTSIDE policy PermitAll match application any set security policies from-zone INSIDE to-zone OUTSIDE policy PermitAll then permit set security policies from-zone OUTSIDE to-zone INSIDE policy PermitAll match source-address any set security policies from-zone OUTSIDE to-zone INSIDE policy PermitAll match destination-address any set security policies from-zone OUTSIDE to-zone INSIDE policy PermitAll match application any set security policies from-zone OUTSIDE to-zone INSIDE policy PermitAll then permit |
Oke anda sudah sampe tahap membentuk topology sesuai dengan gambar diatas, now this time to make it works 😀
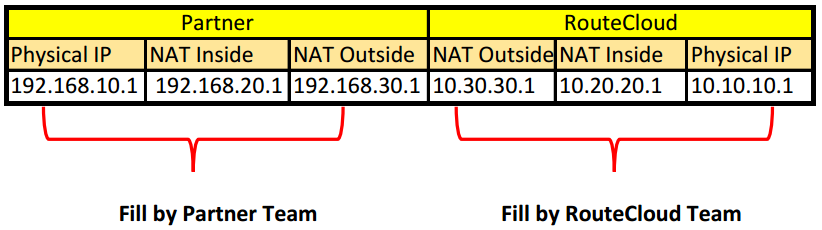
Jadi untuk menyelesaikan case ini, pihak routecloud dan partner perlu ada nya sharing alokasi ip saat ingin menghubungkan sebuah service, jangan sampe terjadi kesalahan alokasi atau maping nat. karena hal tersebut menyebabkan nat tidak akan berjalan sesuai plan hehe.
Tabel diatas adalah bukanlah standar yang baku ya, hehe melainkan map berdasarkan gambaran yang akan kita buat. Jadi begini kira2: Jadi ini adalah flow nya dari Partner ke Routecloud, initial session oleh 192.168.10.1 untuk tujuan ke 10.10.10.1 ip real routecloud, oleh partner team mengalokasikan satu ip yaitu 192.168.20.1, maka session awal adalah 192.168.10.1—>192.168.20.1, selanjutnya partner juga melihat table routecloud bahwa untuk hit ke 10.10.10.1 maka dialokasikan ip nat luar nya adalah 10.30.30.1, sebelum diarah ke situ, FW Partner mentranslasikan ke IP NAT Outside, 192.168.30.1, maka session yang terbentuk adalah 192.168.30.1—>10.30.30.1. Selanjutnya session diterima oleh FW Routecloud, source yang ia terima adalah 192.168.30.1 menuju 10.30.30.1, nah dengan destination nat, akan di map ke NAT Inside 10.20.20.1, oleh si NAT Inside di map ke physical ip 10.10.10.1 dengan source 10.20.20.1. Jadi server 10.10.10.1 menerima initial session dari 10.20.20.1., mudahkan 🙂 🙂
Oke, based on table yang telah kita sepakati, maka config yang akan kita buat adalah sebagai berikut:
FW Partner (FW.CloudB)
NAT Destination:
|
1 2 3 4 5 6 |
root@FW.CloudB# show security nat destination | display set set security nat destination pool 10_30_30_1 address 10.30.30.1/32 set security nat destination rule-set to-tsel from zone TRUST set security nat destination rule-set to-tsel rule 1a match source-address 192.168.10.1/32 set security nat destination rule-set to-tsel rule 1a match destination-address 192.168.20.1/32 set security nat destination rule-set to-tsel rule 1a then destination-nat pool 10_30_30_1 |
Note: baik nat source dan destination, list source-address hanya ada 8, jika lebih anda bisa membuat rule baru dengan ip destination yang sama.
NAT Source:
|
1 2 3 4 5 6 7 8 |
root@FW.CloudB# show security nat source | display set set security nat source pool 192_168_30_1 address 192.168.30.1/32 set security nat source rule-set nat_tsel from zone TRUST set security nat source rule-set nat_tsel to zone UNTRUST set security nat source rule-set nat_tsel rule 2a match source-address 192.168.10.1/32 set security nat source rule-set nat_tsel rule 2a match source-address 192.168.10.0/24 set security nat source rule-set nat_tsel rule 2a match destination-address 10.30.30.1/32 set security nat source rule-set nat_tsel rule 2a then source-nat pool 192_168_30_1 |
Coba anda perhatikan config nat dest dan nat source diatas, related kan dengan table dan flow penjelasannya sebebelumnya. Mari kita lihat config yang ada di FW RouteCloud (FW.CloudA)
NAT Destination:
|
1 2 3 4 5 6 7 |
root@FW.CloudA# show security nat destination | display set set security nat destination pool 10_10_10_1 routing-instance default set security nat destination pool 10_10_10_1 address 10.10.10.1/32 set security nat destination rule-set A from zone OUTSIDE set security nat destination rule-set A rule r1 match source-address 192.168.30.1/32 set security nat destination rule-set A rule r1 match destination-address 10.30.30.1/32 set security nat destination rule-set A rule r1 then destination-nat pool 10_10_10_1 |
Notel: ip pool 10_10_10_1 ada di VRF default inet.0 maka, jika kita menggunakan routing instance perlu kita referensikan juga.
NAT Source:
|
1 2 3 4 5 6 7 |
root@FW.CloudA# show security nat source | display set set security nat source pool 10_20_20_1 address 10.20.20.1/32 set security nat source rule-set A1 from zone OUTSIDE set security nat source rule-set A1 to zone INSIDE set security nat source rule-set A1 rule 1 match source-address 192.168.30.1/32 set security nat source rule-set A1 rule 1 match destination-address 10.10.10.1/32 set security nat source rule-set A1 rule 1 then source-nat pool 10_20_20_1 |
Jika anda sudah merasa yakin, silahkan coba test ping dari ip source yang telah di tentukan. dalam hal ini lakukanlah ping dari source ip 192.168.10.1 ke ip 192.168.20.1. Coba perhatikan dan pelajari session yang terbentuk berikut ini:
FW Partner:
|
1 2 3 4 |
root@FW.CloudB# run show security flow session Session ID: 6787, Policy name: PermitAll/4, Timeout: 2, Valid In: 192.168.10.1/3889 --> 192.168.20.1/3361;icmp, If: ge-0/0/0.0, Pkts: 1, Bytes: 84 Out: 10.30.30.1/3361 --> 192.168.30.1/19641;icmp, If: ge-0/0/1.10, Pkts: 1, Bytes: 84 |
Contoh detail session:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
root@FW.CloudB# run show security flow session extensive Session ID: 6965, Status: Normal Flag: 0x80000000 Policy name: PermitAll/4 Source NAT pool: 192_168_30_1 Dynamic application: junos:UNKNOWN, Encryption: Unknown Application traffic control rule-set: INVALID, Rule: INVALID Maximum timeout: 4, Current timeout: 2 Session State: Valid Start time: 19316, Duration: 2 In: 192.168.10.1/4049 --> 192.168.20.1/3361;icmp, Interface: ge-0/0/0.0, Session token: 0x7, Flag: 0x21 Route: 0xb0010, Gateway: 192.168.1.2, Tunnel: 0 Port sequence: 0, FIN sequence: 0, FIN state: 0, Pkts: 1, Bytes: 84 Out: 10.30.30.1/3361 --> 192.168.30.1/17258;icmp, Interface: ge-0/0/1.10, Session token: 0x6, Flag: 0x20 Route: 0x90010, Gateway: 172.16.10.1, Tunnel: 0 Port sequence: 0, FIN sequence: 0, FIN state: 0, Pkts: 1, Bytes: 84 |
FW RouteCloud:
|
1 2 3 4 5 |
[edit] root@FW.CloudA# run show security flow session Session ID: 4673, Policy name: PermitAll/5, Timeout: 2, Valid In: 192.168.30.1/31116 --> 10.30.30.1/3361;icmp, If: ge-0/0/1.10, Pkts: 1, Bytes: 84 Out: 10.10.10.1/3361 --> 10.20.20.1/30417;icmp, If: ge-0/0/0.1, Pkts: 1, Bytes: 84 |
Mudah2an semakin mudah dipahami ya jika melihat flow session yang terbentuk diatas, dan perlu lihat kedua firewall tersebut supaya lebih jelas 🙂 dan berikut ini contoh session jika kita lakukan ssh.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
root@FW.CloudB# run show security flow session Session ID: 7390, Policy name: PermitAll/4, Timeout: 1794, Valid In: 192.168.10.1/41899 --> 192.168.20.1/22;tcp, If: ge-0/0/0.0, Pkts: 69, Bytes: 7399 Out: 10.30.30.1/22 --> 192.168.30.1/21299;tcp, If: ge-0/0/1.10, Pkts: 47, Bytes: 6663 Total sessions: 1 root@FW.CloudA# run show security flow session Session ID: 1, Policy name: self-traffic-policy/1, Timeout: 60, Valid In: 10.1.1.2/1 --> 224.0.0.5/1;ospf, If: ge-0/0/0.1, Pkts: 2231, Bytes: 178624 Out: 224.0.0.5/1 --> 10.1.1.2/1;ospf, If: .local..0, Pkts: 0, Bytes: 0 Session ID: 5152, Policy name: PermitAll/5, Timeout: 1792, Valid In: 192.168.30.1/21299 --> 10.30.30.1/22;tcp, If: ge-0/0/1.10, Pkts: 69, Bytes: 7399 Out: 10.10.10.1/22 --> 10.20.20.1/29787;tcp, If: ge-0/0/0.1, Pkts: 47, Bytes: 6663 Total sessions: 2 |
Menarik hal diatas, itu contoh satu session di fw routecloud dan partner, jumalah paket dan besarnya paket sama besarnya baik paket in atau paket out.
Oke cukup dulu sebagai contoh penggunaan dual nat di srx.
Komentar