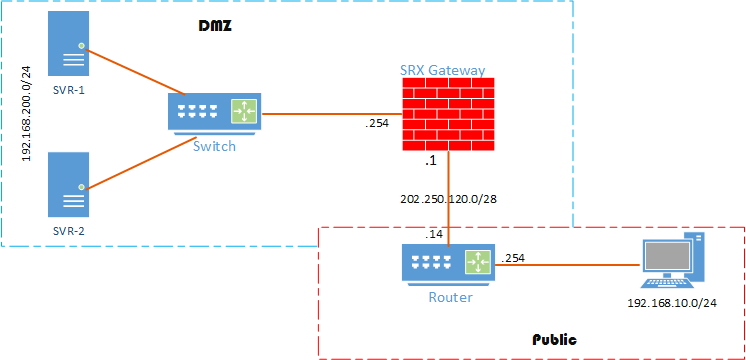
Anda mungkin pernah bertanya, bagaimana private server atau DMZ anda bisa diakses dari internet atau dari public user? jawabannya anda bisa lakukan dengan teknik static nat or dest nat. Lalu apa bedanya static nat dengan dest nat, static nat untuk translasi one-to-one mapping ip address, misalnya dari public user akses ke 8.8.4.4 lalu dengan static nat di mapping ke 172.16.4.4, static nat juga digunakan jika anda memiliki cukup banyak ip, sehingga nanti tidak terjadi overload jika pengguna banyak yang mengakses. Adapun destination nat, untuk translasi or mapping dari satu ip ke banyak ip misalnya, misal dari satu ip 202.250.120.2 port 80 maka akan di map ke 192.168.200.1, atau misal 202.250.120.2 port 3306 maka akan di map ke ip 192.168.200.2. Baik mari kita ikuti contoh design nat berikut.
Sesuai dengan gambar diatas, tulisan ini menekankan pada apa yang bisa dilakukan juniper srx, untk solusi static nat atau destination nat. Untuk lebih jelas nya mari kita lihat satu persatu seperti berikut ini 🙂
Step Konfigurasi awal:
Router:
|
1 2 3 4 5 6 |
set interfaces em1 vlan-tagging set interfaces em1 unit 2 description "Connect to Customer XYZ" set interfaces em1 unit 2 vlan-id 2 set interfaces em1 unit 2 family inet address 202.250.120.14/28 set interfaces em0 unit 0 family inet address 192.168.10.254/24 |
SRX Gateway:
|
1 2 3 4 5 6 7 |
set interfaces ge-0/0/0 vlan-tagging set interfaces ge-0/0/0 unit 2 description "Connect to ISP-X" set interfaces ge-0/0/0 unit 2 vlan-id 2 set interfaces ge-0/0/0 unit 2 family inet address 202.250.120.1/28 set interfaces ge-0/0/2 unit 0 description "Connect to DMZ" set interfaces ge-0/0/2 unit 0 family inet address 192.168.200.254/24 |
vlan-tagging itu dipake jika anda ingin create sub-interface.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
root@FW.CloudB# show security zones security-zone DMZ | display set set security zones security-zone DMZ address-book address 192.168.200.1/32 192.168.200.1/32 set security zones security-zone DMZ address-book address 192.168.200.2/32 192.168.200.2/32 set security zones security-zone DMZ host-inbound-traffic system-services all set security zones security-zone DMZ host-inbound-traffic protocols all set security zones security-zone DMZ interfaces ge-0/0/2.0 [edit] root@FW.CloudB# show security zones security-zone Public | display set set security zones security-zone Public address-book address 202.250.120.2/32 202.250.120.2/32 set security zones security-zone Public address-book address 192.168.10.1/32 192.168.10.1/32 set security zones security-zone Public address-book address 192.168.10.20/32 192.168.10.20/32 set security zones security-zone Public interfaces ge-0/0/0.2 |
Jika anda belum memahami cara create zone atau address book, anda juga bisa melihat postingan ane seblumnya terkait zone disini.
Rule Policy untuk kebutuhan lab ini:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
root@FW.CloudB# ...from-zone Public to-zone DMZ | display set set security policies from-zone Public to-zone DMZ policy SSH_TEST match source-address 192.168.10.1/32 set security policies from-zone Public to-zone DMZ policy SSH_TEST match source-address 192.168.10.20/32 set security policies from-zone Public to-zone DMZ policy SSH_TEST match destination-address 192.168.200.1/32 set security policies from-zone Public to-zone DMZ policy SSH_TEST match destination-address 192.168.200.2/32 set security policies from-zone Public to-zone DMZ policy SSH_TEST match application junos-ssh set security policies from-zone Public to-zone DMZ policy SSH_TEST match application junos-icmp-all set security policies from-zone Public to-zone DMZ policy SSH_TEST then permit set security policies from-zone Public to-zone DMZ policy HTTP_TEST match source-address any set security policies from-zone Public to-zone DMZ policy HTTP_TEST match destination-address 192.168.200.1/32 set security policies from-zone Public to-zone DMZ policy HTTP_TEST match destination-address 192.168.200.2/32 set security policies from-zone Public to-zone DMZ policy HTTP_TEST match application junos-http set security policies from-zone Public to-zone DMZ policy HTTP_TEST match application junos-https set security policies from-zone Public to-zone DMZ policy HTTP_TEST then permit set security policies from-zone Public to-zone DMZ policy AnyDMZ match source-address any set security policies from-zone Public to-zone DMZ policy AnyDMZ match destination-address any set security policies from-zone Public to-zone DMZ policy AnyDMZ match application any set security policies from-zone Public to-zone DMZ policy AnyDMZ then permit |
Itu rule terakhir masih ada any, tidak masalah karena ini masih tahap lab or testing, jika anda ingin membuat rule spesifik, diatas juga sudah ada contoh yang bisa anda ikuti. Anda juga bisa bloking trafik yang ke arah ip device yang belum dialokasikan untuk nat. rule policy nya dari public zone ke device srx itu sendiri dalam hal ini dikenal sebagai junos-host zone. Rule yang ke arah junos-host zone adalah sebetulnya tidak kelihatan or implist accept, maka bisa kita buat jadi deny sperti dibawah:
|
1 2 3 4 |
set security policies from-zone Public to-zone junos-host policy Deny match source-address any set security policies from-zone Public to-zone junos-host policy Deny match destination-address any set security policies from-zone Public to-zone junos-host policy Deny match application any set security policies from-zone Public to-zone junos-host policy Deny then deny |
Jangan lupa proxy arp, jika ip nat yang digunakan adalah ip yang yang sama dengan interface network.
|
1 |
set security nat proxy-arp interface ge-0/0/0.2 address 202.250.120.2/32 to 202.250.120.13/32 |
Solusi 1: Menggunakan Static NAT
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
set security nat static rule-set static-nat from zone Public set security nat static rule-set static-nat rule nat-svr1 match destination-address 202.250.120.2/32 set security nat static rule-set static-nat rule nat-svr1 then static-nat prefix 192.168.200.1/32 set security nat static rule-set static-nat rule nat-svr2 match destination-address 202.250.120.3/32 set security nat static rule-set static-nat rule nat-svr2 then static-nat prefix 192.168.200.2/32 Output: root@FW.CloudB> show configuration security nat static rule-set static-nat { from zone Public; rule nat-svr1 { match { destination-address 202.250.120.2/32; } then { static-nat { prefix { 192.168.200.1/32; } } } } rule nat-svr2 { match { destination-address 202.250.120.3/32; } then { static-nat { prefix { 192.168.200.2/32; } } } } } |
Untuk nat di juniper, ada namanya rule-set yang terdiri dari rule-rule nat. jadi dalam satu rule-set anda bisa membuat berbagai teknik nat, dalam hal ini misalnya static nat. pada kesempatan diatas, maping yang dilakukan dari satu ip ke satu ip yang lain. sebagai contoh diatas, public user akses ip luar nya 10.250.120.2 maka dengan static nat, akan di forward ke ip 192.168.200.1, tidak ada maping spesifik port disini. artinya juka user public akses port 22 maka yang di forward ke ip internal juga port 22, port translation tidak berjalan disini. Mari kita lihat contoh session nya.
Maka session nya seperti berikut:
|
1 2 3 4 5 |
root@FW.CloudB> show security flow session Session ID: 187572, Policy name: SSH_TEST/6, Timeout: 1666, Valid In: 192.168.10.1/38834 --> 202.250.120.2/22;tcp, If: ge-0/0/0.2, Pkts: 27, Bytes: 4007 Out: 192.168.200.1/22 --> 192.168.10.1/38834;tcp, If: ge-0/0/2.0, Pkts: 27, Bytes: 4131 Total sessions: 1 |
contoh session port 80.
|
1 2 3 4 5 6 7 8 |
root@FW.CloudB# run show security flow session Session ID: 108, Policy name: HTTP_TEST/7, Timeout: 298, Valid In: 192.168.10.1/34890 --> 202.250.120.3/80;tcp, If: ge-0/0/0.2, Pkts: 12, Bytes: 2082 Out: 192.168.200.2/80 --> 192.168.10.1/34890;tcp, If: ge-0/0/2.0, Pkts: 19, Bytes: 22402 Session ID: 109, Policy name: HTTP_TEST/7, Timeout: 296, Valid In: 192.168.10.1/34892 --> 202.250.120.3/80;tcp, If: ge-0/0/0.2, Pkts: 6, Bytes: 895 Out: 192.168.200.2/80 --> 192.168.10.1/34892;tcp, If: ge-0/0/2.0, Pkts: 7, Bytes: 6886 |
Nah mari kita coba sedikit merubah config static, contoh perubahannya seperti berikut:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
set security nat static rule-set static-nat rule nat-svr2 match destination-address 202.250.120.3/32 set security nat static rule-set static-nat rule nat-svr2 match destination-port 8080 set security nat static rule-set static-nat rule nat-svr2 then static-nat prefix 192.168.200.2/32 set security nat static rule-set static-nat rule nat-svr2 then static-nat prefix mapped-port 80 output: root@FW.CloudB#show security nat static rule-set static-nat rule nat-svr2 match { destination-address 202.250.120.3/32; destination-port 8080; } then { static-nat { prefix { 192.168.200.2/32; mapped-port 80; } } } |
Dari hasil perubahan diatas, maka session yang terbentuk jika diakses port 8080 adalah seperti berikut:
|
1 2 3 4 5 6 7 8 |
root@FW.CloudB# run show security flow session Session ID: 220, Policy name: HTTP_TEST/7, Timeout: 298, Valid In: 192.168.10.1/39962 --> 202.250.120.3/8080;tcp, If: ge-0/0/0.2, Pkts: 8, Bytes: 1345 Out: 192.168.200.2/80 --> 192.168.10.1/39962;tcp, If: ge-0/0/2.0, Pkts: 18, Bytes: 22174 Session ID: 221, Policy name: HTTP_TEST/7, Timeout: 298, Valid In: 192.168.10.1/39964 --> 202.250.120.3/8080;tcp, If: ge-0/0/0.2, Pkts: 6, Bytes: 789 Out: 192.168.200.2/80 --> 192.168.10.1/39964;tcp, If: ge-0/0/2.0, Pkts: 14, Bytes: 17945 |
Untuk melihat proses translasi sukses atau tidak nya juga anda bisa menggunakan teknik berikut:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
root@FW.CloudB> show security nat static rule all Total static-nat rules: 2 Total referenced IPv4/IPv6 ip-prefixes: 4/0 Static NAT rule: nat-svr1 Rule-set: static-nat Rule-Id : 1 Rule position : 1 From zone : Public Destination addresses : 202.250.120.2 Destination ports : 20022 - 20030 Host addresses : 192.168.200.1 Host ports : 22 - 30 Netmask : 32 Host routing-instance : N/A Translation hits : 0 Successful sessions : 0 Failed sessions : 0 Number of sessions : 0 Static NAT rule: nat-svr2 Rule-set: static-nat Rule-Id : 2 Rule position : 2 From zone : Public Destination addresses : 202.250.120.3 Host addresses : 192.168.200.2 Netmask : 32 Host routing-instance : N/A Translation hits : 0 Successful sessions : 0 Failed sessions : 0 Number of sessions : 0 |
translation hits 0 ini menunjukkan tidak ada proses tranlasi yang terjadi. Jika ada proses translasi maka hasil nya bisa seperti berikut:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
root@FW.CloudB# run show security nat static rule all Total static-nat rules: 2 Total referenced IPv4/IPv6 ip-prefixes: 4/0 Static NAT rule: nat-svr1 Rule-set: static-nat Rule-Id : 1 Rule position : 1 From zone : Public Destination addresses : 202.250.120.2 Host addresses : 192.168.200.1 Netmask : 32 Host routing-instance : N/A Translation hits : 7 Successful sessions : 7 Failed sessions : 0 Number of sessions : 0 Static NAT rule: nat-svr2 Rule-set: static-nat Rule-Id : 2 Rule position : 2 From zone : Public Destination addresses : 202.250.120.3 Destination ports : 8080 - 8080 Host addresses : 192.168.200.2 Host ports : 80 - 80 Netmask : 32 Host routing-instance : N/A Translation hits : 19 Successful sessions : 19 Failed sessions : 0 Number of sessions : 6 |
Solusi 2: Menggunakan Destination NAT
Opsi config destination nat:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
[edit security nat destination rule-set D-NAT rule rule2] root@FW.CloudB# set match ? Possible completions: + application + apply-groups Groups from which to inherit configuration data + apply-groups-except Don't inherit configuration data from these groups > destination-address Destination address > destination-address-name Address from address book > destination-port Destination port + protocol IP Protocol + source-address Source address + source-address-name Address/address-set from address book [edit security nat destination rule-set D-NAT rule rule2] root@FW.CloudB# set match |
anda bisa mespesifikan di rule nat, segmen atau host source, destination maupun port, di destination nat juga anda juga perlu create ip pool destination.
Oke mari kita lihat contoh rule dest nat dengan source any.
|
1 2 3 4 |
set security nat destination pool 192_168_200_2 address 192.168.200.2/32 set security nat destination rule-set D-NAT from zone Public set security nat destination rule-set D-NAT rule rule2 match destination-address 202.250.120.3/32 set security nat destination rule-set D-NAT rule rule2 then destination-nat pool 192_168_200_2 |
source any anda tidak perlu men-set nya atau bisa juga di set 0.0.0.0/0 ini juga berti dari any-ipv4.
Contoh flow session:
|
1 2 3 4 |
root@FW.CloudB# run show security flow session Session ID: 618, Policy name: SSH_TEST/6, Timeout: 2, Valid In: 192.168.10.1/3 --> 202.250.120.3/5550;icmp, If: ge-0/0/0.2, Pkts: 1, Bytes: 84 Out: 192.168.200.2/5550 --> 192.168.10.1/3;icmp, If: ge-0/0/2.0, Pkts: 1, Bytes: 84 |
Jika anda ingin mecoba untuk mapping port, maka coba anda lihat config berikut:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
[edit security nat destination rule-set D-NAT rule rule2] root@FW.CloudB# show match { destination-address 202.250.120.3/32; destination-port { 8080 to 8090; } } then { destination-nat { pool { 192_168_200_2; } } } |
jika port ditranlasi juga maka di nat kita biasa kenal dengan PAT (port address translation). Anda juga men-set spesifik port ip poolnya. contoh nya sperti berikut:
|
1 2 |
set security nat destination pool 192_168_200_2 address 192.168.200.2/32 set security nat destination pool 192_168_200_2 address port 80 |
Mari kita lihat contoh session berikut
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
root@FW.CloudB# run show security flow session Session ID: 1000, Policy name: HTTP_TEST/7, Timeout: 2, Valid In: 192.168.10.1/40168 --> 202.250.120.3/8080;tcp, If: ge-0/0/0.2, Pkts: 11, Bytes: 2656 Out: 192.168.200.2/80 --> 192.168.10.1/40168;tcp, If: ge-0/0/2.0, Pkts: 30, Bytes: 34485 Session ID: 1001, Policy name: HTTP_TEST/7, Timeout: 2, Valid In: 192.168.10.1/40170 --> 202.250.120.3/8080;tcp, If: ge-0/0/0.2, Pkts: 12, Bytes: 2743 Out: 192.168.200.2/80 --> 192.168.10.1/40170;tcp, If: ge-0/0/2.0, Pkts: 26, Bytes: 31734 root@FW.CloudB# run show security flow session Session ID: 1008, Policy name: HTTP_TEST/7, Timeout: 2, Valid In: 192.168.10.1/53266 --> 202.250.120.3/8085;tcp, If: ge-0/0/0.2, Pkts: 20, Bytes: 3981 Out: 192.168.200.2/80 --> 192.168.10.1/53266;tcp, If: ge-0/0/2.0, Pkts: 68, Bytes: 90450 Session ID: 1009, Policy name: HTTP_TEST/7, Timeout: 2, Valid In: 192.168.10.1/53268 --> 202.250.120.3/8085;tcp, If: ge-0/0/0.2, Pkts: 6, Bytes: 943 Out: 192.168.200.2/80 --> 192.168.10.1/53268;tcp, If: ge-0/0/2.0, Pkts: 9, Bytes: 6990 |
Anda bisa melihat flow session diatas, contoh hit port yang berbeda, tetapi di forward ke satu port. Dengan destination ip yang sama, service yang berbeda anda bisa mapping ke internal ip dengan ip yang sama port yang sama, ip yang sama port yang berbeda atau bahkan ip yang beda dengan port yang sama atau beda. Anda bisa lakukan dengan nat destination. Jadi disni anda bisa lebih hemat banyak ip tentunya.
Sebagai contoh perhatikan config berikut:
|
1 2 3 4 5 6 |
set security nat destination pool 192_168_200_3 address 192.168.200.3/32 set security nat destination pool 192_168_200_3 address port 445 set security nat destination rule-set D-NAT rule rule3 match destination-address 202.250.120.3/32 set security nat destination rule-set D-NAT rule rule3 match destination-port 3300 to 3310 set security nat destination rule-set D-NAT rule rule3 then destination-nat pool 192_168_200_3 |
anda bisa set dengan satu port saja atau menggunakan range port itu anda juga bisa melakukannya, maka session yang terbentuk adalah sebagai berikut:
|
1 2 3 4 5 6 7 8 |
root@FW.CloudB# run show security flow session Session ID: 1422, Policy name: AnyDMZ/8, Timeout: 1758, Valid In: 192.168.10.1/59822 --> 202.250.120.3/3310;tcp, If: ge-0/0/0.2, Pkts: 2, Bytes: 112 Out: 192.168.200.3/445 --> 192.168.10.1/59822;tcp, If: ge-0/0/2.0, Pkts: 1, Bytes: 60 Session ID: 1444, Policy name: AnyDMZ/8, Timeout: 1794, Valid In: 192.168.10.1/42994 --> 202.250.120.3/3306;tcp, If: ge-0/0/0.2, Pkts: 2, Bytes: 112 Out: 192.168.200.3/445 --> 192.168.10.1/42994;tcp, If: ge-0/0/2.0, Pkts: 1, Bytes: 60 |
jadi diatas adalah contoh hit ip yang sama, port yang berbeda kemudian di map ke ip yang berbeda dengan port yang berbeda 🙂 Oke cukup sekian ya, next artikel adalah bagaimana menggunakan nat source dan destination untuk satu session paket (nat inbound and outbound). Jika ada pertanyaan silahkan komentar dibawah atau bisa email ke bunyamin@routecloud.net
Komentar